Despite the fact that Google I/O is a developers conference, it always gets the attention of journalists and consumers as well. The reason is simple: this is when Google shows its brand-new features, services, and products that will be changing our lives in the near future. Let’s take a look at the most important of them from a security angle.
1. Android M: customizable app permissions
The first big thing Google presented at San Francisco this year is Android M, where M stands for… “M developer preview” at the moment. The final release is rather distant; most likely to happen in the fall. The first new feature you definitely want to know about is the fully customizable app permissions policy.
In current versions of Android you need to grant a whole set of permissions when you install an app. And these apps are not modest: many of them want access to your camera, microphone, list of contacts, SMS, and so on. The only choice you have is to grant permissions or don’t install the app at all.
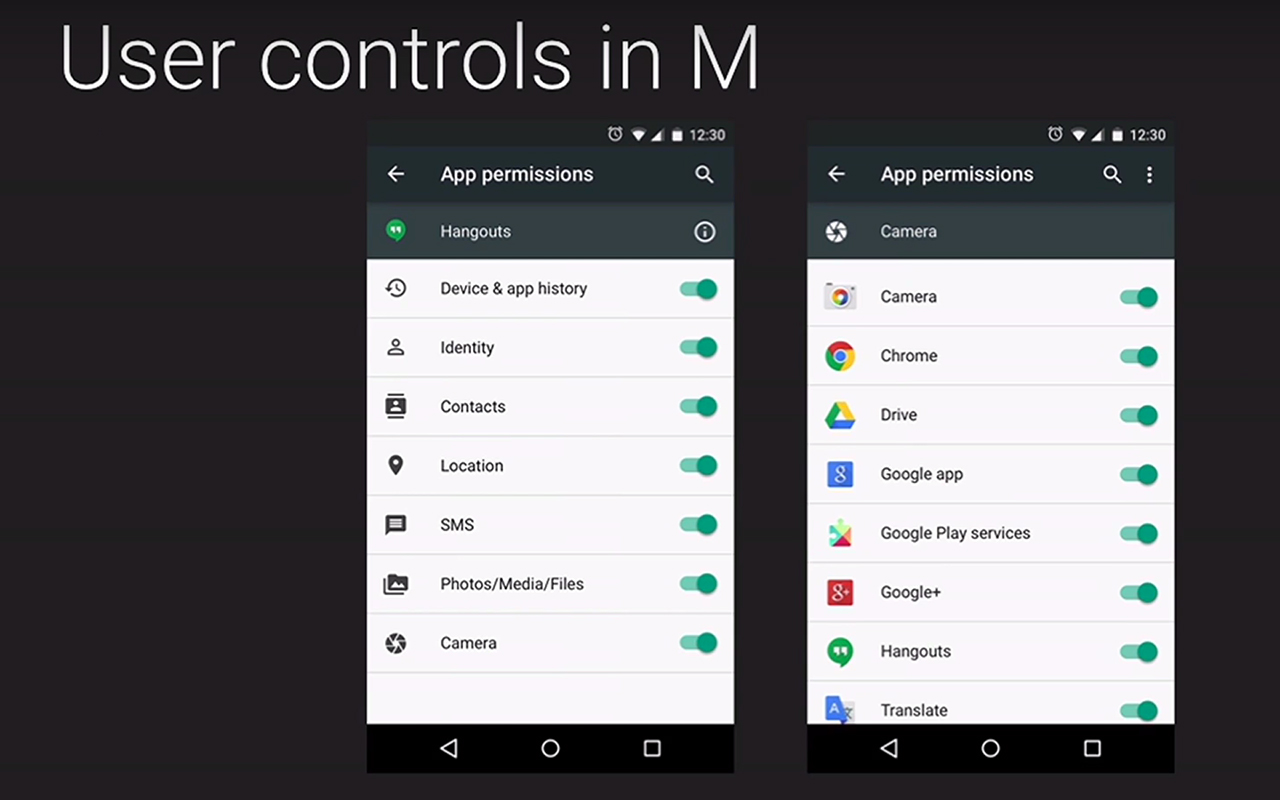
New Android M’s approach is that any permissions should be asked and granted (or rejected) on demand, not when you install the app. Moreover, there is a ‘permissions manager’ in Android M and you can easily watch all app permissions and switch on or off any that you choose. You’ll also be able to look for some specific permission, say, camera access, and set this list precisely the way you like it — for instance, you can switch off camera access for all apps.
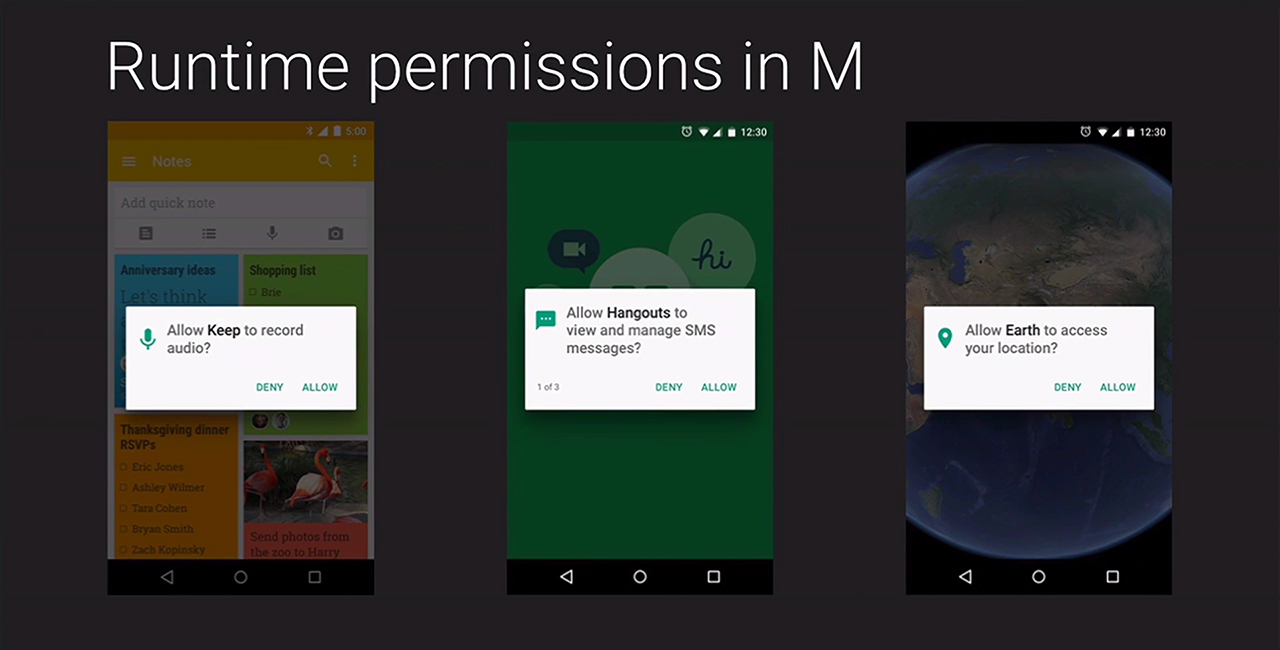
This was good news. The great news is that this customizable permissions policy won’t be limited to the apps designed for Android M specifically, it should work with the legacy apps as well! So, finally we will have freedom to choose how much of our privacy we want to give away to apps developers. It’s a great instrument for people who care about their privacy and a new intricate puzzle for people who don’t.
2. Android M: Now on Tap
Currently, Google Now collects data from Google services you use: it grabs it from your Gmail, from your searches, from your location, and so on. That will change very soon: one of the features introduced in Android M is Now on Tap. This feature will allow Google to grab the data from any app and use it to give you hints and advices.
So, now it’s official: Google will get your data from 3rd party apps. On the bright side, the company will utilize this data to make your life more convenient – as it always does.
3. Google Photos
From now on, Google Photos is not a part of Google+, but a standalone app and service. It has lots of new features to store and organize all your photos – literally all your photos: cloud storage is free and unlimited for all images up to 16 megapixels and all videos up to 1080p.
Yep, Google wants you to store your whole life in the company’s cloud. Powerful face recognition included (hey, they can recognize even infants!), as well as other funny things like geotagging and timestamps organization.
Here is a cloud storage services price/value roundup. Protect your data on Android: https://t.co/9YctXUcoCQ #io15 pic.twitter.com/Euikq0bgaL
— Kaspersky Lab (@kaspersky) May 29, 2015
5. Fingerprint sensors API
There’s already a number of Android smartphones with fingerprint sensors, but any manufacturer who wants to implement this feature needs to do it on its own. With Android M, it should be much easier to make fingerprint enabled gizmos because the next-gen version of Google’s mobile OS has built-in support for these sensors, and interfaces for fingerprint-based authentication in apps and services without actually giving your fingerprint to anyone except Google itself.
It is debatable how secure the fingerprint protection is. But without question it is way more secure than no password, or PIN, or other protection at all – which is still the most popular solution among common users.
5. Android Pay
Speaking of protection, all users would really like to protect their money. And it’s essential since Google introduced its new mobile payments system called Android Pay. In a few words, it’s much like Apple Pay, but from Google. It works via NFC only (unlike Samsung Pay which can be used with legacy POS terminals) and allows in-apps purchases as well.

Moreover, you can use Android Pay not only to store your credit or debit cards, but loyalty and bonus cards and coupons as well. Of course, you can use any of them to make a payment. And if you’re wondering what happened with Google Wallet, here’s the answer: it will remain, but only for person-to-person payments.

6. Google hands-free payments
And there’s more news for payments: Google has a really crazy new feature which the company will test in partnership with McDonalds and Papa Johns in San Francisco Bay Area. They call it ‘Hands-free payments’ and it works like this: customers download an app, and when checking out at a store, they don’t need even to take out the phone. All they have to do is stand in front of the cash register and say ‘I’d like to pay with Google’.
Unfortunately, it’s unclear how exactly this feature works and what technologies are involved to secure the payment.
7. Brillo: the IoT software platform
A lot has been said about Internet of Things and how insecure it is. One of the concerns is that manufacturers of these connected devices usually base their gizmos on some general purpose Linux-based software platforms, which they customize poorly and rarely update.
Google is ready to offer a solution for this problem. It’s called Brillo and it is a software platform for IoT devices. The platform is based on Android with a somewhat reduced features list and functionality tuned in the way, which is more suitable for IoT devices.
The Empire strikes back and forth: 7 things you should know about #AndroidM and other new #Google features #IO15
Tweet
There are at least two pieces of good news here: First, this is a tailor-made platform from one of the leading software companies. Second, it most likely will get updates on time. Bad news is that if the industry adopts this platform, we will miss the good old days when we thought ‘ubiquitous’ about having Google in our phones and PCs.




Source: kaspersky.com




