One fine (or not so fine) day, you check your inbox and discover a message that starts like this:
“I’m aware, ********** is your password. You don’t know me and you are probably thinking why you are getting this email, right? Well, I actually placed a malware on the adult video clips (porn) web site…”
Or like this:
“I hacked this mailbox and infected your operating system with a virus…”
Or even:
“I’m part of an international hacker group. As you can guess, your account was hacked…”
All sorts of variants exist, but the message boils down to a claim that the sender infected your computer by hacking your account or placing malware on a porn site you visited. They appear to have harvested your e-mail contacts, social networks, instant messengers, and phone book. They appear to have total access to your device, and they’ve also, it appears, hijacked your webcam to make a video of you watching something.
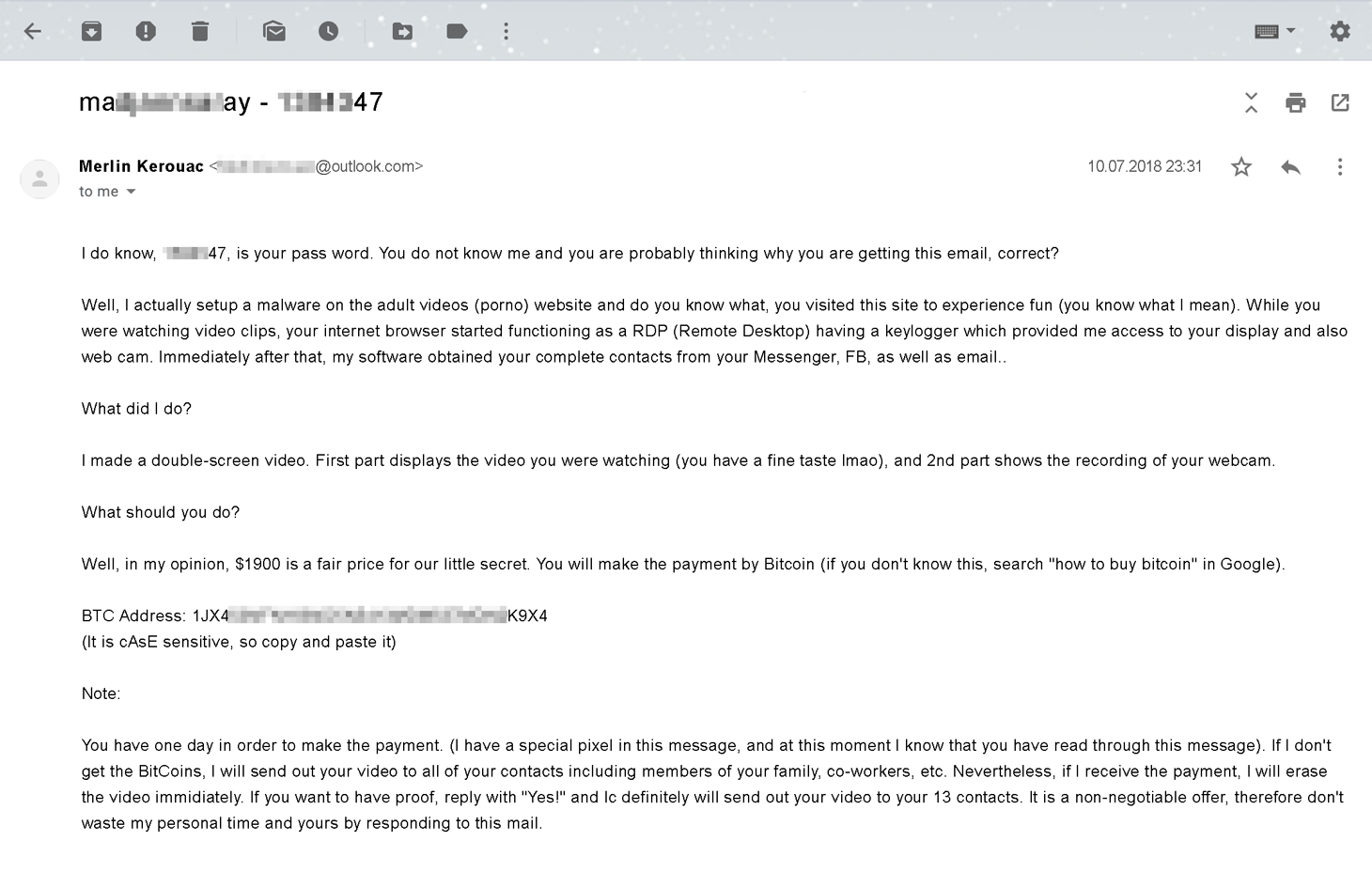
The cybercriminals threaten to send the video to all of your friends and colleagues. The only way to stop them, they say, is to transfer a specified sum of cryptocurrency to an anonymous wallet.
Some scammers give you only a few days, claiming to know exactly when you opened the e-mail, which supposedly contains a tracking pixel that lets them monitor the message’s status. In some cases, as part of their effort to convince you of the existence of a compromising video, you are asked to reply to the message, whereupon the scammers say they will send the video to a selection of your contacts.
Of course, they say if payment is made, they’ll immediately destroy the video and the database of your contacts.
Calm down, no one’s filmed you
In reality, there is no omnipotent “virus” or shameful video. How does someone know your password? Simple: The blackmailer has got hold of one of the many databases of user accounts and passwords available on the darknet, leaked from a variety of online services. Alas, such leaks are not uncommon — in the United States alone, no fewer than 163 million user records were compromised in just the first three quarters of 2017.
As for “knowing” that you’ve been viewing adult content, it’s a shot in the dark. The e-mail you received was sent to thousands, perhaps millions of people, with the addressee’s password (and other personal details) automatically merged into the message from the database. Even if only a few dozen recipients pay up, that will be more than enough for the scammer.
The same goes for the promise to send a video to some of your friends as proof. Few people would want to verify the existence of such delicate material in this manner. Most would prefer not to risk even a limited disclosure of this kind of secret.
Ransom message — with a bonus Trojan encryptor
Recently, scammers have come up with an even more effective way to make victims pay up: In early December, researchers at Proofpoint found a spam wave offering victims to personally verify the existence of an embarrassing video without involving family and friends. All they had to do was follow the link in the message.
Naturally, no video appeared. Instead, users were prompted to download a ZIP archive, which if unpacked and run really did infect the system — big time.
Don’t worry, cybercriminals still won’t be filming you watching porn. What they do, however, is encrypt your files with the GandCrab malware, and demand more ransom — this time, to recover your data.
How to stay safe
To avoid falling victim to ransomware scammers, we advise being cautious and following a few simple steps. Here’s what you don’t want to do:
- Don’t panic.
- Don’t pay the ransom.
- Don’t respond to ransom e-mails — you will only validate your address and attract more.
- Don’t follow links in such messages. At best, you’ll get bombarded with shady ads, and you might even infect your machine with a virus, now for real.
What to do:
- Note the password sent in the ransom e-mail, and change it immediately on any websites where you use it. While you’re at it, choose a stronger password.
- Use a reliable password manager, such as Kaspersky Password Manager, to store your strong, hard-to-remember passwords.
- Install a trusty antivirus to keep malware off your system and set to rest any worries about webcam hijacking.
Source: kaspersky.com




