The predictability of human beings can barely be overestimated. This predictability can be easily exploited when it comes to things like passwords, secret words, PIN codes and more. Many of us use names, dates of birth and another easy-to-guess things as passwords, not to mention really obvious crap like ‘12345’ that is still surprisingly popular. What about lock screen patterns, are we predictable as well when we’re creating them? As it turns out — we are.

Researcher Marte Løge from Norwegian company Itera, have made an analysis, what patterns people are actually creating when they are asked to do it for three instances: shopping app, smartphone lock screen and online banking respectively. The results are quite startling.
Firstly, there’s a strong relation between type of the app one wants to lock and strength of the pattern. People tend to use less strong patterns for smartphones lock screen then they use for online banking and even shopping apps.
How predictable are screen #lock #patterns and how to create the most #reliable one
Tweet
Secondly, lots of people, about 10% of the thousands surveyed by Løge, are using letters-like patterns, which are complete analog of such crappy passwords like’12345′ and by any means can’t be considered strong enough to protect anything.
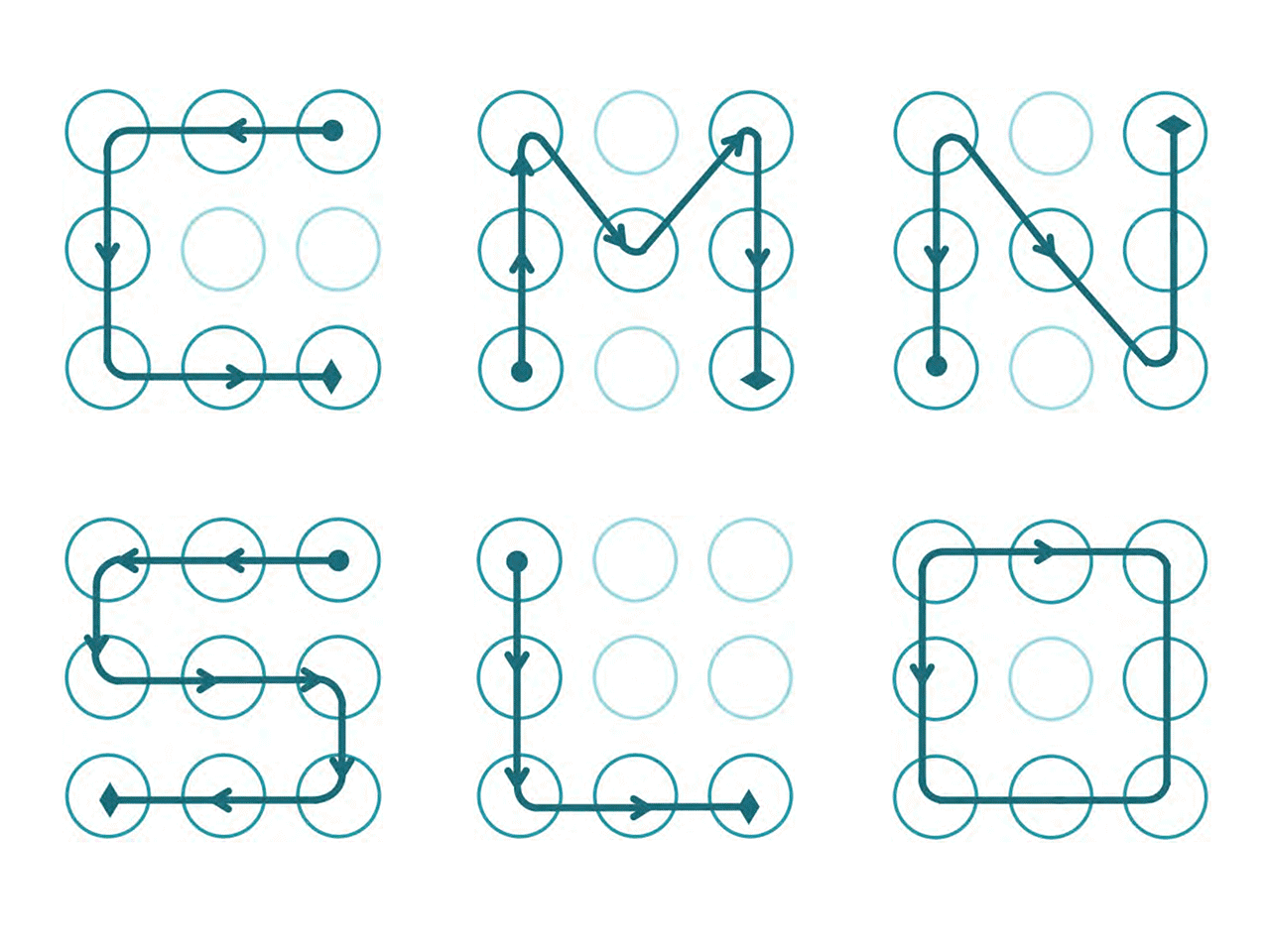
Letters-like patterns are the worst and the most easy-to-guess
Thirdly, there are approximately 390,000 combinations that a hacker can guess, but the number of combinations can be shrunk due to the human factor. The majority of the combinations mentioned above contain eight or nine points, unfortunately these are not used. Instead the actual pool is roughly 100,000 combinations.
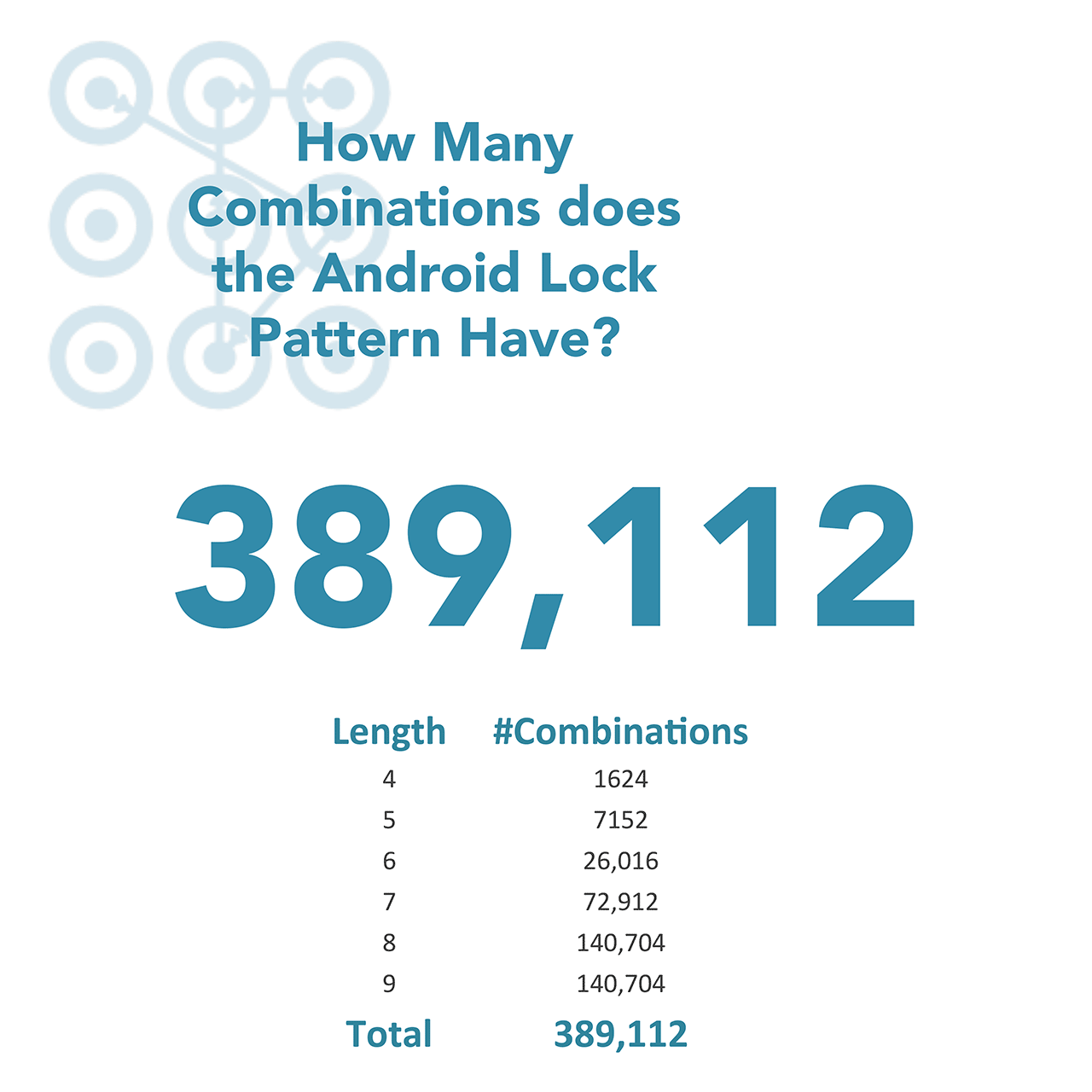
Despite the fact the overall number looks pretty good, about 3/4 of all combinations correspond to 8- and 9-points patterns which are rarely used by people
An average length for all patterns in research is about 5 — that is not good enough to protect the smartphone or app. This length gives you about 7,000 of possible combinations, and thus obviously is even weaker than simple 4-digits PIN-code. And the most popular length is 4, which stands for just 1,600 of combinations.
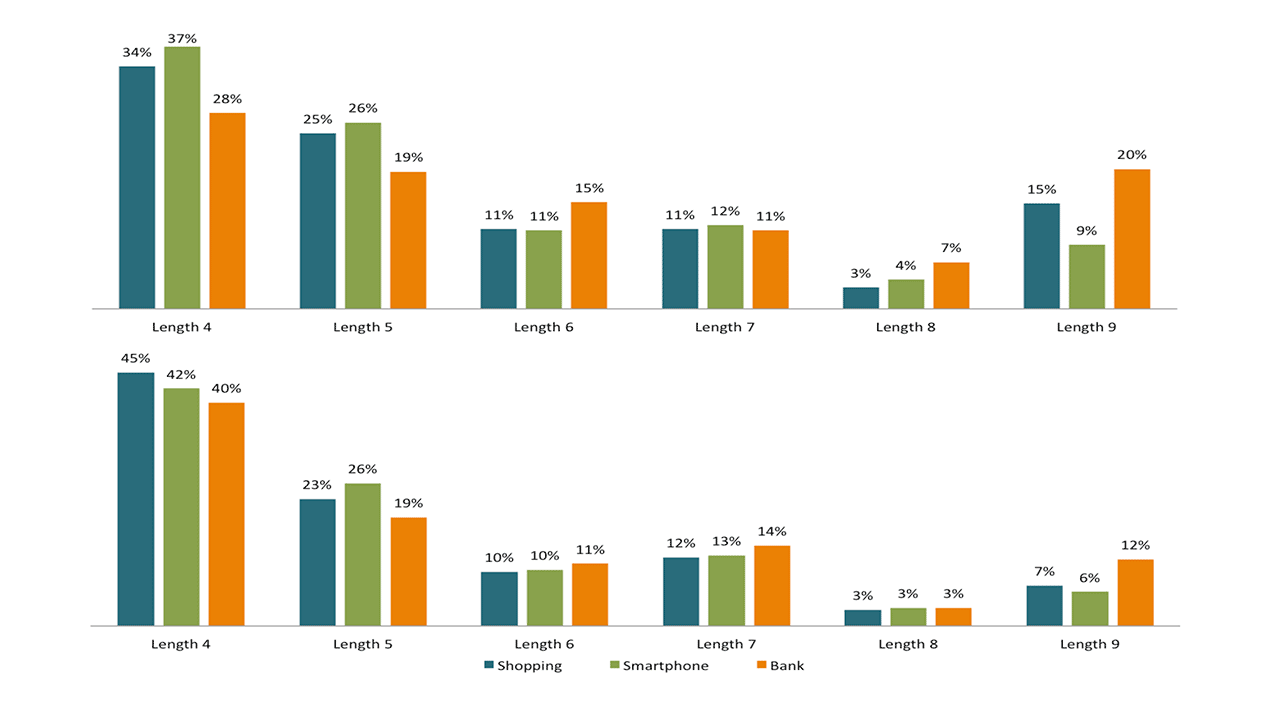
Patterns of length 4 are the most popular
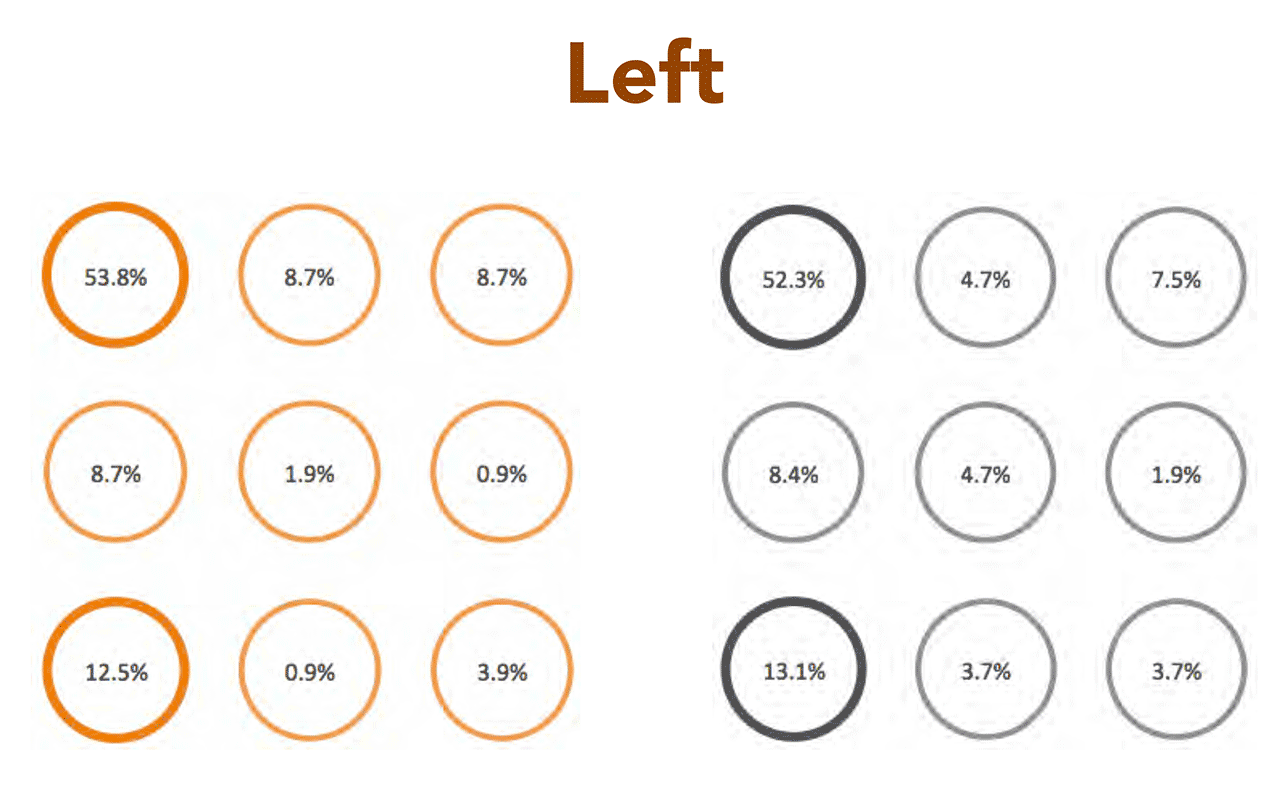
Moreover, to reduce the count of combinations to even much lower numbers, you can easily predict the starting point of a pattern. People tend to use corners as a first point, about a half of all patterns have starting point in upper-left corner. Combined with lower-left and upper-right corners it gives you 73% of all combinations people are actually using.
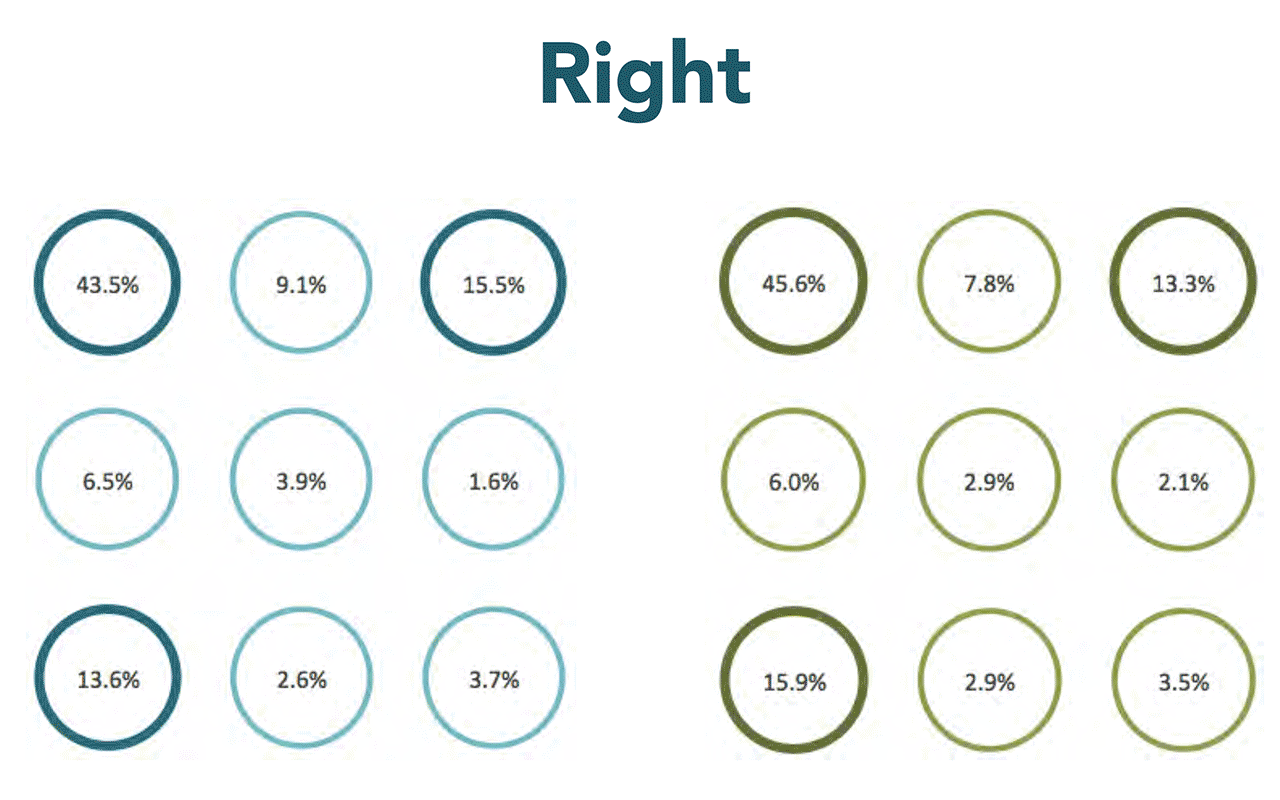
Curiously, it almost doesn’t matter if you’re talking about right or left-handed person, and if the smartphone is used with one hand (likely for smaller screens) or with two hands (likely for bigger screens). The numbers are very close.
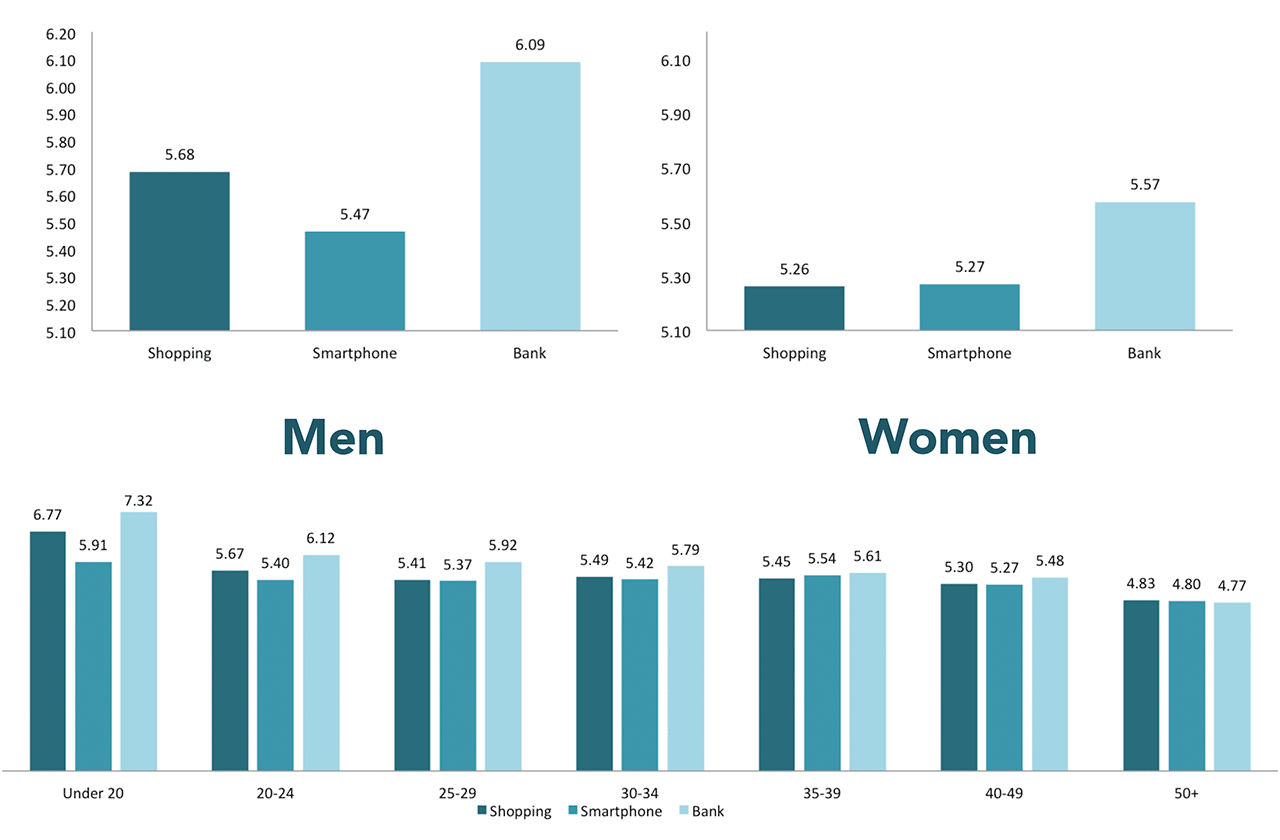
Another curious fact is that women tend to use weaker patterns than men. And the age of a person also matters: the younger you are, more likely you use stronger pattern. So, knowledge of sex and age of person can really help to predict the pattern that he or she uses.
What can we learn from this research? Basically, if you’re using patterns for Android screen lock or some sensitive apps, and you want to really protect your data, the best strategy is to act like nobody does. And these are our advices:
- Never use obvious combinations such as letters-like patterns. Using that weak pattern is pretty close to using no pattern or password at all.
- Use one of the starting points rarely used: the best one is in the middle of the right side. The lower-right corner is pretty good as well.
- The best lengths for a pattern are 8-points or 9-points: firstly it gives you a huge number of possible combinations; secondly these lengths are the least popular.
- And of course, consider switching to password from patterns. It may be easier to remember password, even long and reliable one, than strong enough pattern.
How long would it take for your password to be cracked? https://t.co/9nLxWV1Ghu #security #themoreyouknow #it #smb pic.twitter.com/JmwqNtpsq6
— Kaspersky Lab (@kaspersky) August 3, 2015
Source: kaspersky.com




