Recently, you’ve probably been drowning in messages from every service you’ve ever used informing of changes to privacy policies and the need to resubscribe to their newsletters in order to carry on receiving them.
No, it’s not an international flash mob of global companies — they’re just trying to fall in line with the EU’s new General Data Protection Regulation (GDPR), which came into force on May 25, 2018.
The GDPR applies to all companies operating in the territory of the EU, and requires them to handle user data responsibly, which includes storing it securely, not transferring it to anyone without the users permission, and providing timely notifications about leaks in case they happen.
What’s more, companies do not have the right to send messages to users without their consent. That’s why your mailbox is full of resubscription requests — services are keen to keep sending you stuff, but can’t do so without that OK from you, which they are desperately trying to get.
GDPR fraud
Cybercriminals sniffed a perfect opportunity to make quite some user data out of this situation. After all, millions of people worldwide are blindly clicking “Yes, I agree” in countless messages and entering personal info on multiple sites without a second thought.
For example, we came across a mailshot seemingly on behalf of Apple menacingly informing recipients that their Apple ID is locked and set to be deleted in three days unless they fill out a form to confirm their account information.
Apple is unable to confirm your billing details, the message said, and this allegedly violates the company’s security policy. Your account is frozen and will be deleted within three days, continued the warning, unless you follow the link and enter your data.
This, of course, has nothing to do with Apple. Just plain phishing.
The authors of the mailshot employed the oldest social engineering trick in the book: intimidation. Afraid of parting company with such a precious account, the less savvy user panics and acts rashly, entering data in places where it shouldn’t. Such scams are as effective as they are numerous, i.e. very.
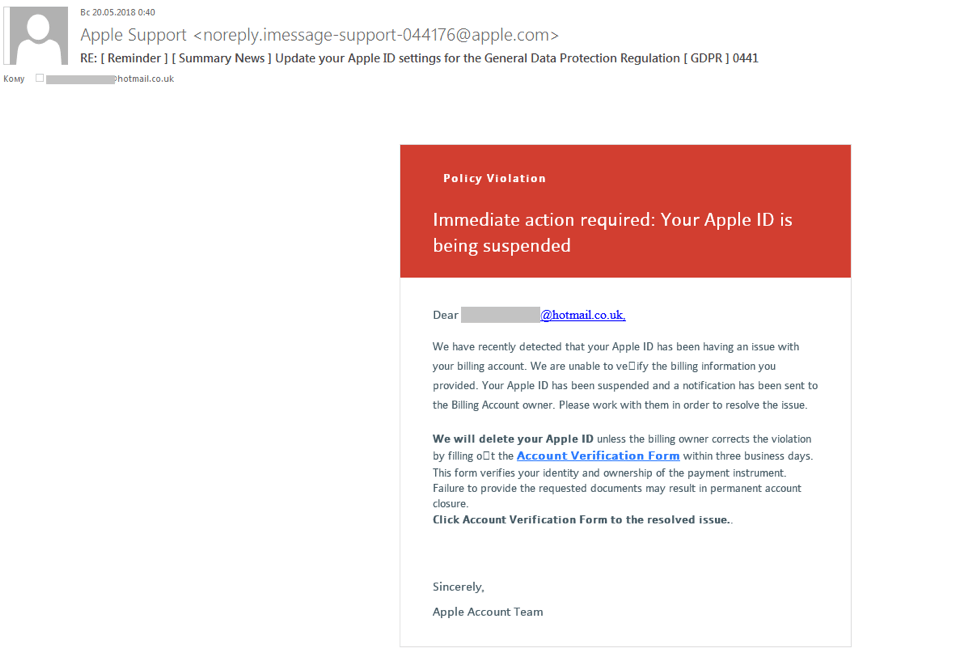
Example of a GDPR-related phishing email on behalf of Apple
How to spot phishing
If you keep a cool head, it’s fairly easy to see that you’re being phished. Let’s take a closer look at this Apple ID-related message.
In most cases, it’s possible to determine that it’s fraud even without opening it. For example, look at the sender’s address in the From field and the topic in the Subject field (see screenshot). There is something obviously fake about a long email address containing generic words and a sequence of numbers, especially when you know that all legitimate messages about the Apple ID account come from [email protected].
The message subject also contains strange numbers that don’t make any sense. Spammers use them to create information noise and make the message look unique. Also pay attention to the RE tag, which means that the received message is a reply to a message that you sent. This is highly suspicious if you never wrote to this company (again, this is done to bypass spam filters).
If the subject and sender’s address aren’t enough, an analysis of the message text should dispel all doubts. No self-respecting company in possession of your personal data will ever address you using your email address instead of your first and last names.
Another way to recognize a fraudulent email is to look at the address of the link that you are being asked to follow. If you hover the mouse cursor over the text of the link, the address it points to will appear nearby or in the bottom-left corner of the browser window. It should not contain any strange domains or short links, such as bit.ly or similar.
How to protect your data
- Never enter personal data on suspicious sites. All actions involving personal data should be performed on official company websites.
- Before clicking on a link in a message and agreeing to provide personal information, make sure that the message is genuine. Check the sender’s address, subject, and text for anything untoward. If something looks odd, don’t click on anything. Contact the technical support team of the service in whose name the message was sent. They will help clarify the situation.
- Use a reliable security solution, such as Kaspersky Internet Security, with anti-spam and anti-phishing components. It will sift out dubious messages and give warning of suspicious links.
Source: kaspersky.com




