Last week, we talked about desktop ransomware, which is certainly nasty stuff. Ransomware is found not only on desktops, but also on mobile devices — and it is also on the rise there.
Today we are going to discuss the most prevalent types of mobile ransomware. We obtained the statistics in this post from our security solutions.
What is mobile ransomware?
A lot of people already know what ransomware is — and awareness is only growing. The most widespread — and most annoying — type of desktop ransomware is the cryptolocker, malware that encrypts your data and offers to restore it if you pay ransom. Another type of ransomware, the blocker, blocks either browsers or operating systems from working and demands a ransom to return access. Nowadays, desktop blockers are less widespread than cryptoransomware, mostly because the latter is more efficient at funneling money into the hands of criminals.
The threat landscape on mobile devices, however, is just the opposite: Almost no cryptolockers exist for Android devices because the operating system and apps make cloud backups. When users have their files backed up, there’s no need to pay ransom, and therefore creators have little incentive to attack Android users.
Blockers are the much more popular means to infect Android devices. On mobiles, they act simply by overlaying the interface of every app with their own, so a victim can’t use any application at all. PC owners can get rid of a blocker with relative ease — all they need to do is remove the hard drive, plug it into another computer, and wipe out the blocker’s files. But you can’t simply remove the main storage from your phone — it’s soldered onto the motherboard. That explains why blockers hold 99% of the mobile ransomware “market.”
Little big players
In 2014–2015 four main actors dominated the mobile ransomware scene: Svpeng, Pletor, Small, and Fusob. At this time, Pletor has almost stopped its expansion; its creators have launched the infamous Acecard Trojan and seem to be pouring their resources into developing and spreading that instead. The developers of Svpeng have also refocused, mostly on the banking version of the Trojan. That leaves only two big mobile ransomware families, Small and Fusob. As a result, in 2015–2016 these two Trojans represent more than 93% of the mobile ransomware space.
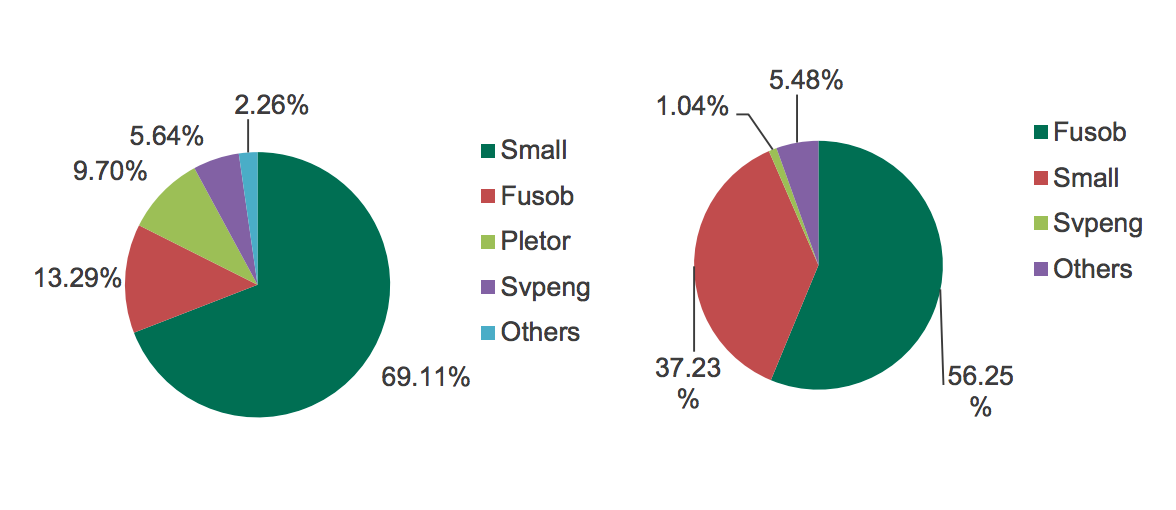
It’s noteworthy that the Fusob and Small Trojan families have a lot in common. Both display fake screens that pretend to be signed by authorities and accuse the victims of misdemeanor. Both say that a criminal case will be opened unless the user pays the fine.
Both Fusob and Small also offer rather strange ways to pay the ransom: Fusob suggests payment with iTunes gift cards, whereas Small offers victims the option of paying by the Kiwi payment system or with MoneyPak xpress Packet vouchers. Both were probably created by some Russian-speaking groups of cybercriminals, but with very different approaches.
Fusob first detects the device’s language, and if it is one of the post-Soviet republic languages, Fusob simply does nothing. Otherwise, it shows a screen that claims to come from the NSA and demands ransom — from $100 to $200. The majority of Fusob’s victims (more than 41%) live in Germany; the United Kingdom and the United States hold the second and third places, with 14.5% and 11.4%.
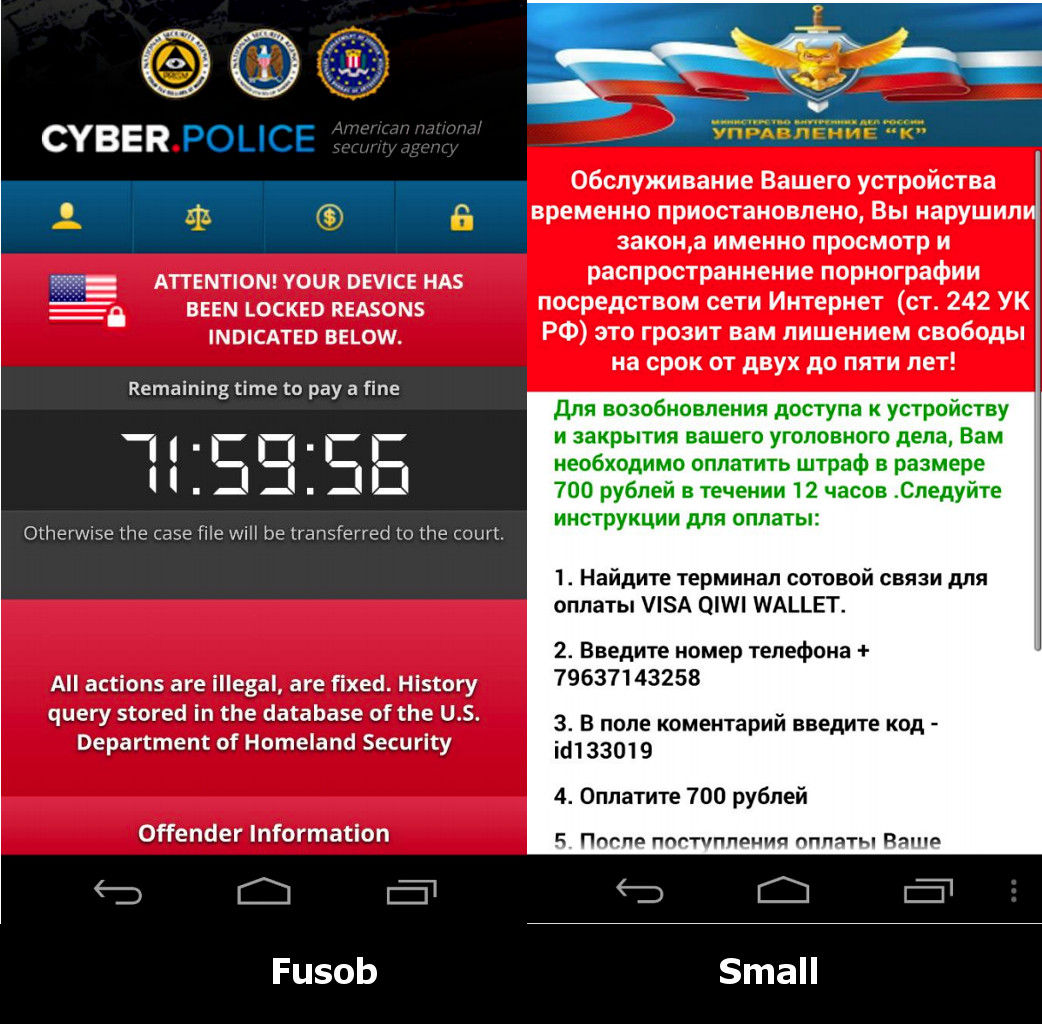
Then, there’s the Small family. Almost 99% of Small’s victims are located in three of the countries that Fusob avoids: Russia, Kazakhstan, and Ukraine. Small ransomware shows a government-themed screen with payment instructions, threats, and a demand for 700–3,500 rubles ($10 to $50) to unlock the infected device. An English-locale version of Small also exists — it has a different block-screen that mentions the FBI and demands about $300.
There are two more versions of Small. One is a cryptolocker that performs the same operations the first version does, and on top of that encrypts the files on the device’s SD card. The second is a multifunction Trojan that is capable of stealing money, siphoning data, and, of course, locking the device.
What’s going on and what to expect
Back when mobile malware was not such a big deal, we began sounding the alarm about it. Just as we have predicted, this form of malware is experiencing an explosive growth rate — and it shows no signs of deceleration. Between 2014 and the present, mobile attacks have almost quadrupled!
The number of ransomware victims among them also grew — it more than doubled, from 2.04% to 4.63%. Last year, the United States represented the main target for mobile ransomware — one out of 10 users who encountered malware found it in the form of mobile ransomware. Now it’s two in 10 in both Germany and Canada, about one in seven in the United Kingdom, the United States, and Kazakhstan, and more than one in 10 in Italy and the Netherlands.
Well-maintained backup solution is an impt part of your protection from Cryptolocker ransomware both on PC & Android. http://t.co/ZifMqg4EsI
— Kaspersky Lab (@kaspersky) June 11, 2014
We expect mobile malware — mobile ransomware in particular — to become even more popular next year. To read a more detailed report on ransomware, visit securelist.com.
How to protect yourself
1. Install applications only from official shops such as Google Play. To be sure that no application makes its way onto your device from an untrusted source, go to Android settings, choose Security, and make sure that the “Unknown Sources” box is not checked.
2. Regularly update your device’s firmware and its installed apps. You can choose to update apps automatically, but you still have to update the system manually — and it’s better to do that as soon as an over-the-air (OTA) update arrives.
3. Install a strong security solution. Even if you’ve installed all possible updates and downloaded apps from official sources only, you haven’t eliminated the risk completely. Malware can lurk in Google Play and can also spread by means of exploit kits using yet-unknown vulnerabilities. To avoid falling victim to mobile ransomware, we recommend using the full version of Kaspersky Internet Security for Android, because only that version constantly monitors what’s happening on your device and eliminates threats as soon as they emerge.
Source: kaspersky.com



