Ransomware became one of the most convenient rackets for cybercriminals. On reading recent news on the GameOver Zues botnet we found out that its owners were also actively distributing the CryptoLockerransomware, which encrypts the victim’s files and asks for ransom in a case when Zeus banking trojan did not have any success while on rampage in your PC. A similar scheme is now gaining traction on smartphones: iOS-based devices are blocked with the help of the Apple’s Find My iPhone service, while for Android smartphones the culprits have coded a mobile version of Cryptolocker, Pletor.a. Unfortunately, the news resources tend to serve such information lavishly seasoned with panic, and you are very likely to have seen headlines like ‘Only Two Weeks to Protect Your Computers from a Dreadful Threat’. You need not panic; just know your enemy and follow our protection action plan.
Why Cryptolocker and its likes are dangerous
Unlike previous examples of “blockers“, which used to just block the PC screen to disturb your PC experience, cryptolockers, as is read in the name, encrypt the user’s files.
Even having managed to delete the malware, you cannot continue working with your files.
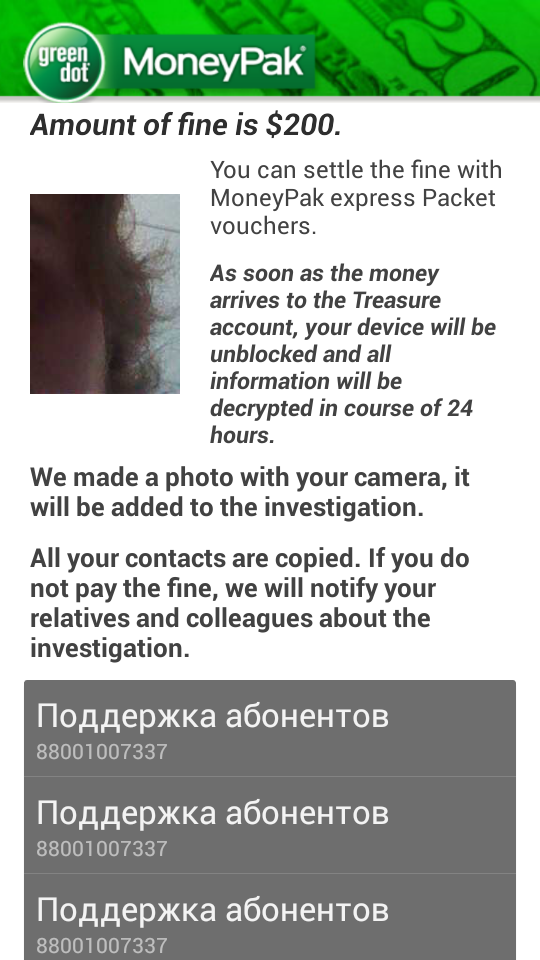
It means that, even having managed to delete the malware, you cannot continue working with your files. A number of such lockers, owing to mistakes and imperfections in their code, are quite likely to be deciphered by third-party anti-virus utilities. With regard to better-crafted samples of cryptolockers, they use strong encryption and do not store the key on the affected PC, making user-initiated deciphering impossible, keeping this opportunity open only for the cybecriminals (who, obviously, demand $50-2000 for this “service”). This approach is now used on Android devices: Back in May, we discovered the Pletor.a ransomware, which is able to encrypt files stored on an SD card and place a threatening message on a display, asking for a ransom. Current Pletor versions do have the aforementioned flaw, so third parties (read: antivirus companies, e.g. us) are able to help the victim with file deciphering, but as of today, there are more than 30 modifications of this ransomware, and the version which does not allow for third-party deciphering, might be just around the corner.
New “milking” scheme for cybercriminals: First, steal your banking credentials, then encrypt your files and demand a ransom.
Tweet
Also, last week in the US we have discovered a new version of mobile banking Trojan Svpeng, which is evidently walking in GameOver Zeus’s shoes. The current version is able to efficiently block the device, demanding a ransom. Additionally, the malware’s code shows developers’ intent to steal financial data from the smartphone and contains a link to a not yet implemented Cryptor method, which is likely to offer the file blocking capability to the cybercriminals. Curiously, not only do mobile Trojans encrypt the files, but blackmail the user with mailing the compromising text messages or photos along the victim’s contact list. That means the bleeders now have one more trick in their sleeve.

Protecting your PC from Cryptolocker, PrisonLocker, Cryptowall and their likes
- Check your PC for Zeus-type malware. Use the free Kaspersky Lab utility which is able to scan the PC and delete the malware.
- Install a strong Internet security solution. It will prevent compromising in the future.
- Create an online backup copy of your data. It will be needed in case your PC is affected by Cryptolocker. Instead of paying ransom for your encrypted data, you just need to restore it. The backup will also save you in case of fire, hard drive failure and other unfortunate circumstances. It is vital to perform a regular backup on your PC. For the online backup plan, instant synchronization is possible, for locally stored backup copy we recommend daily synchronization. To ensure better protection from Cryptolocker, all external storage devices must be disconnected after the backup has been performed.
Well-maintained backup solution is an important part of your protection from Cryptolocker ransomware both on PC and Android.
Tweet
Protecting a smartphone from the Pletor.a ransomware and Svpeng ransomware
- Install a robust antivirus app from Google Play or other trusted app store like Yandex.Store;
- In security settings, disable the third-party app installation support;
- Do not download apps from forums, third-party websites, etc. Use only trusted sources.
- On installation, keep an eye on access rights the app is asking for. Traditionally, rights to send text messages or making calls are considered suspicious, yet the right which must immediately attract your attention is the right to modify the content of the SD card. Unfortunately, it is a very popular right used by many games, dictionaries and other legitimate software. So the decision must not be taken based only on the application access rights. If you disabled automatic scanning for the newly installed apps, run the antivirus on each new app installation.
- Use Google Drive, Dropbox and other cloud storage and backup solution to backup your photos and other documents.
Beware of fake ‘cures’
Cybercriminals went as far as using the news on Cryptolocker and GameOver Zeus to their advantage. The spam offering utilities for malware deletion and post-Cryptolocker file deciphering is already distributed online. Those who download the utility, being lured into it by its seeming ease of use and freeware nature, are doomed to have even more malware on their PCs. So we recommend using only trusted applications from the trusted suppliers to cure your systems from Cryptolocker.
Protect your smartphone now

Source: kaspersky.com