Turla APT group, also known as Snake and Uroboros, is one the most advanced threat actors in the world. This cyber espionage group has been active for more than 8 years, but little was known about its operations until last year, when we published our Epic Turla research.

Specifically, this research included examples of language artifacts, showing that part of the Turla are Russian-speakers. These people employ codepage 1251, which is commonly used to render Cyrillic characters, and words like ‘Zagruzchik,’ which means, “boot loader” in Russian.
What makes the Turla group especially dangerous and difficult to catch is not just the complexity of its tools, but the exquisite satellite-based command-and-control (C&C) mechanism implemented in the final stages of the attack.
RT @rogeragrimes: Kaspersky analysis of Epic Turla http://t.co/jGQAVZylzu
— Kaspersky Lab (@kaspersky) August 12, 2014
Command-and-control servers are the base of advanced cyber-attacks. At the same time, it’s the weakest link in malicious infrastructure, and is always targeted by digital investigators and law enforcement agencies.
There are two good reasons for that. Firstly, these servers are used to control all of the operations. If you could shut them down, you could disturb or even disrupt the cyber campaign. Secondly, C&C servers can be used to trace attackers back to their physical locations.
That’s why threat actors are always trying to hide C&C as deep as possible. The Turla group has found quite effective way to do it: they conceal servers’ IPs in the sky.
Epic Turla:massive #cyberespionage operation penetrates EU/Mideast spy agencies via @kaspersky http://t.co/vmWvteVmq1 pic.twitter.com/1wuNL7SoFn
— Adolfo Hernández (@Adolfo_Hdez) August 8, 2014
One of the most widespread and inexpensive types of satellite-based Internet connection is a downstream-only connection. In this case, outgoing data from a user’s PC is carried via conventional lines — a wired or cellular, — while all the incoming traffic comes from the satellite.
However, this technology has one peculiarity: all the downstream traffic comes from the satellite to the PC unencrypted. Simply put, anyone can intercept the traffic. The Turla group uses this flaw in a new and quite interesting way: to hide their own C&C traffic.
Russian-speaking cyber spies exploit satellites #Turla
Tweet
What exactly they do is the following:
- They listen to the downstream from the satellite to identify active IP addresses of satellite-based Internet users who are online at that moment.
- Then they choose a number of currently active IP addresses to be used for masking a C&C server without the legitimate user’s knowledge.
- The machines infected by Turla get the instruction to send all the data to the chosen IPs. The data travels through conventional lines to the satellite and finally down from the satellite to the users with the chosen IPs.
- This data is dropped by legitimate users’ PCs as garbage, while threat actors pick it from downstream satellite connection.
Since satellite downstream covers a wide area, it’s impossible to track where exactly threat actors’ receivers are physically based. To make this game of cat and mouse even harder, the Turla group tends to exploit satellite Internet providers located in Middle Eastern and African countries such as Congo, Lebanon, Libya, Niger, Nigeria, Somalia or the UAE.
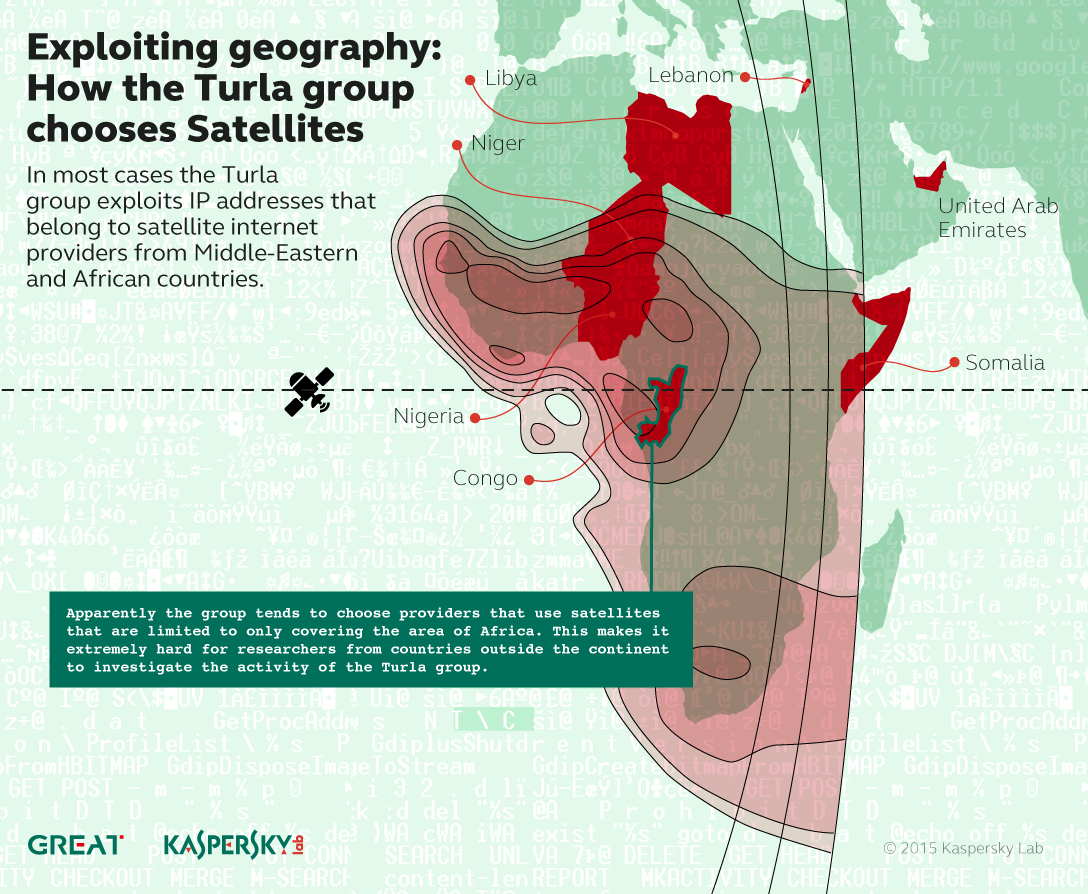
Satellite beams that are used by operators in these countries usually do not cover European and North American territories, making it very hard for most of security researchers to investigate such attacks.
The attackers behind Turla have infected hundreds of computers in more than 45 countries including Kazakhstan, Russia, China, Vietnam and the United States. Organizations of interest for Turla group include government institutions and embassies, as well as military, education, research and pharmaceutical companies.
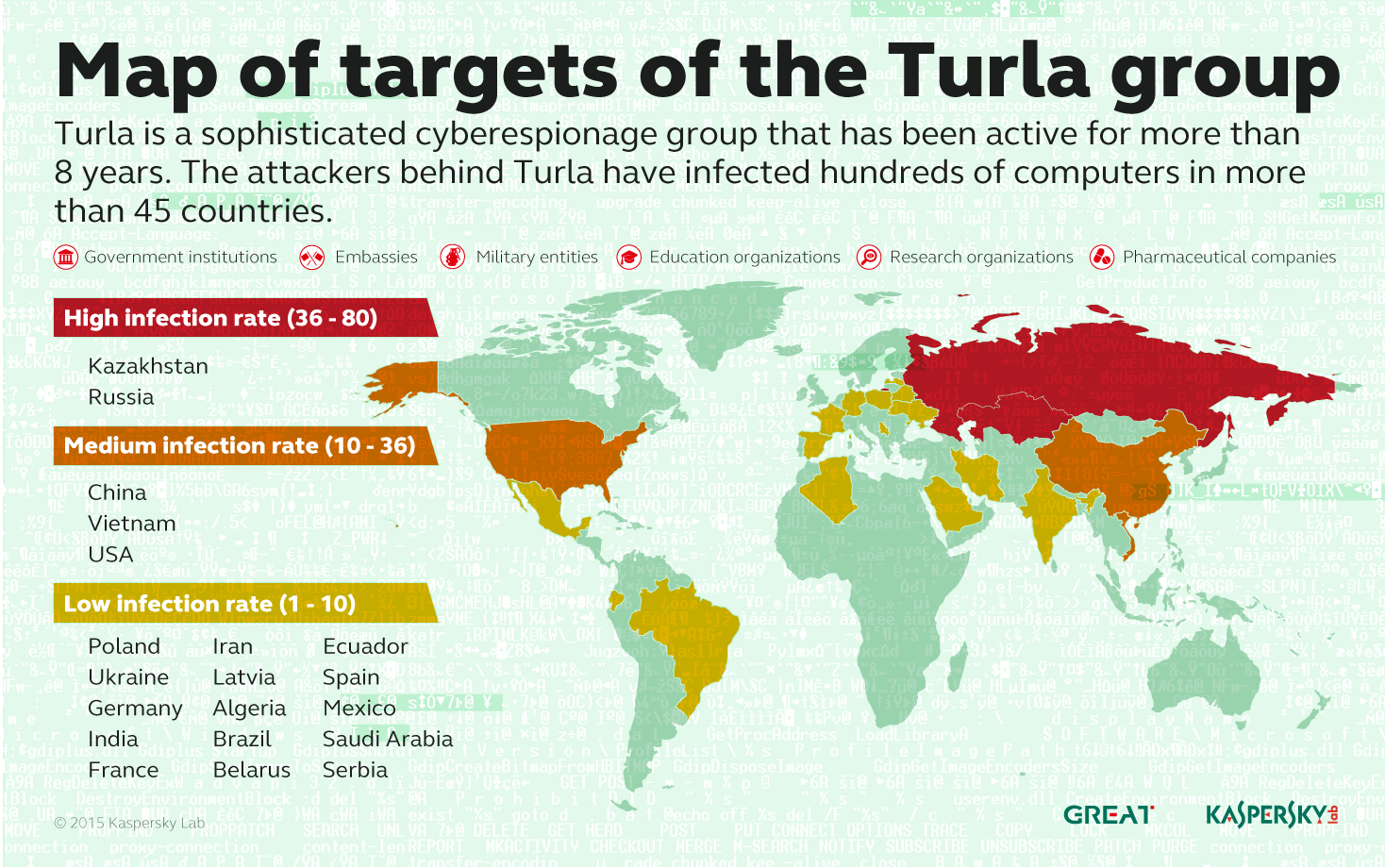
This was the bad news. The good news for our users is that Kaspersky Lab products successfully detect and block the malware used by the Turla threat actor.
Source: kaspersky.com



