Cybercriminals are learning from each other. Take TeslaCrypt, for example. It is a relatively new family of ransomware; its samples were first detected in February 2015. The notable feature of the early TeslaCrypt versions was that malware was targeting not only usual sets of files, including documents, pictures and videos, but games-related file types as well. By that time, it was a rather weak malware due to a couple of its technical flaws.

Despite the fact malware creators scared their victims with the frightful RSA-2048 algorithm, in reality the encryption was not that strong. Moreover, during the encryption process the malware stored encryption keys in a file on the victim’s computer hard drive, making it possible to save the key by interrupting the encryptor’s operation, or to extract the key before the respective area of the disk was overwritten.
But, as was mentioned above, criminals are learning. In the latest TeslaCrypt 2.0 version, which was recently discovered by Kaspersky Lab researchers, malware creators have implemented some new features preventing decryption of stolen files and discovery of malware’s command&control servers.
The best line of #defense against any #ransomware is to have backed up your machines yesterday. https://t.co/cpcBqX1Qy2
— Kaspersky Lab (@kaspersky) January 30, 2015
First, they’ve adopted the sophisticated elliptic curve encryption algorithm from creators of the famous and very troublesome CTB-Locker ransomware. Secondly, they’ve changed the method of key storaging: now they are using the system registry instead of a file on disk.
Thirdly, TeslaCrypt creators have stolen the web page which victims see after their files have been encrypted from another ransomware family, CryptoWall. Of course, all payment credentials are changed, but the rest of the text, which is very effective from a ‘selling’ point of view, is fully copied. By the way, the ransom is rather large: about $500 at the current bitcoin exchange rate.
Malware from the TeslaCrypt family is known to be distributed using exploit kits such as Angler, Sweet Orange, and Nuclear. This method of distributing malware works as follows: When a victim visits an infected website, an exploit’s malicious code uses vulnerabilities in the browser (usually in plugins) to install target malware in the system.
#TeslaCrypt 2.0 #ransomware: stronger and more complicated
Tweet
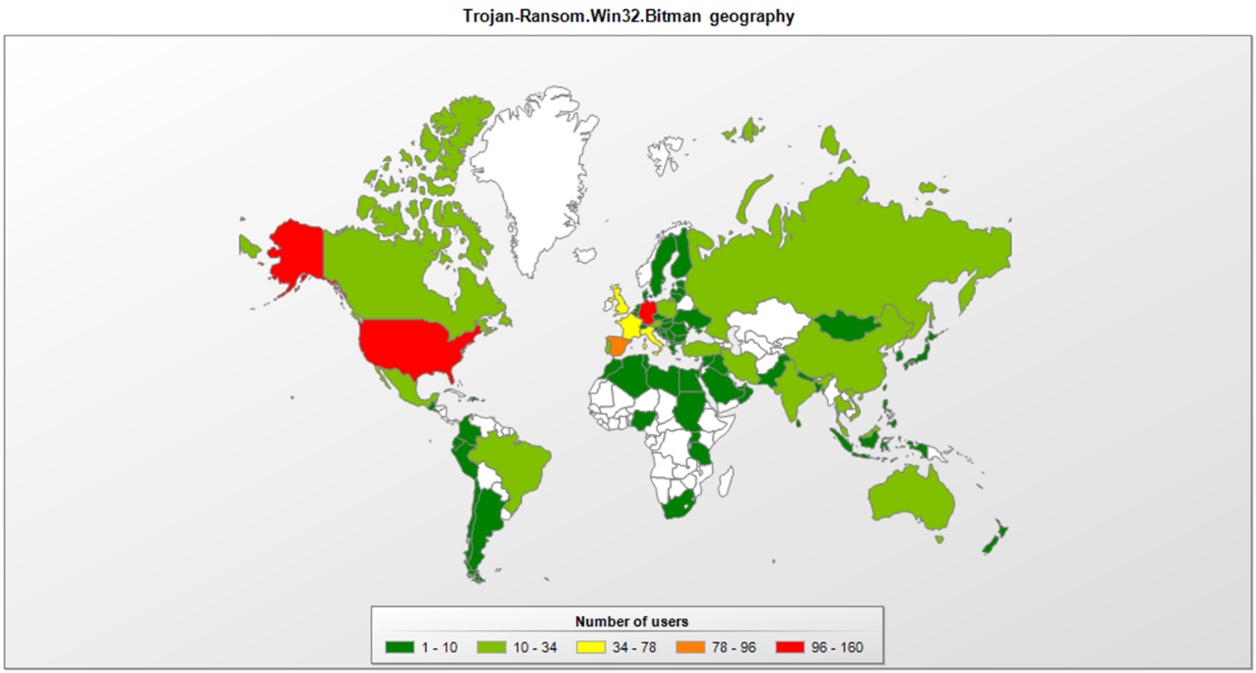
The most affected countries include USA, Germany, UK, France, Italy, and Spain. Kaspersky Lab products detect malware from the TeslaCrypt family, including the latest version discussed above, as Trojan-Ransom.Win32.Bitman. So, our users are not in danger.
Our recommendations on counteracting this and other families of ransomware include the following:
- Create backup copies of all your important files on a regular basis. Copies should be kept on media that are physically disconnected immediately after the backup copying is completed. The last part is important, because the TeslaCrypt and other types of malware encrypt connected drives and network folders as well as the local hard drive.
- It is crucially important to update your software in a timely fashion, especially the web browser and its plugins.
- In case a malicious program lands on your system, it will be best addressed by the latest version of a security software with updated databases and activated security modules.
Source: kaspersky.com



