RIPS employees disclosed the details new vulnerability in WordPress. The bug was found in the CMS itself, and not in a popular plugin or theme, which happens not so often. There is no official patch for this flaw yet, although the developers were informed about the bug back in November last year.
The problem found is that a user with access to the post editor can also upload and delete images and previews for them. As a result, such a user is able to inject arbitrary malicious code into WordPress and delete files critical for the operation of the CMS, which under normal conditions should only be available to the administrator on the server or via FTP. Although only a user who already has access to it can attack a vulnerable resource, RIPS experts warn that even the lowest rights will be enough . In theory, even User-level access is enough to elevate privileges and exploit a vulnerability.
At the root of the problem lies the fact that an attacker can delete the wp-config.php file. After that, he gets the opportunity to re-initiate the installation process, using his own settings and, for example, forcing the site to distribute malware or other malicious content. A video demonstration of the attack can be seen below.
According to RIPS, The vulnerability poses a threat to all versions of the CMS, including the most recent – WordPress 4.9.6.
WordPress representatives have not yet commented on the lack of a patch for the new bug. In this regard, the journalists of BleepingComputer turned to Sucuri specialists for a “second opinion”, and they confirmed to the publication that all conclusions in the RIPS report are justified and the problem found is indeed dangerous.
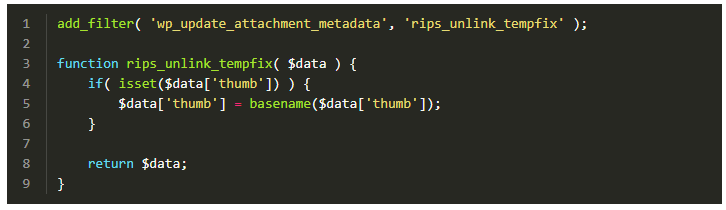
Although there is no official fix yet, the RIPS developers have released their own temporary hotfix, which is attached to the report. The specialist code must be added to the functions.php file.
Source: xaker.ru




