Look around — we are living in the Internet of Things. In our day-to-day life, we encounter things connected to the Internet, starting with our home Wi-Fi routers and leading up to traffic light management systems and street security cameras. Since they are connected, all of them can be found in two worlds — both in the real world and in the Web.

And like there is Google to help you find the data you are looking for on the Internet, there are also special search engines that help you find these connected devices. Say hello to Shodan and Censys!
Shodan is the first (and probably the foremost) search engine for the Internet of Things — it’s been around for more than 7 years. It was named after the main antagonist in the computer game series System Shock — a highly villainous artificial intelligence called Shodan. Real-world Shodan is not as relentless, but it is capable of doing harm. But before we get to the bad news, let’s find out how does the search engine actually work.
Nice wrap up of #IoT-related talks at #TheSAS2015: “Internet of Crappy Things: https://t.co/ORygHSJs9W
— Eugene Kaspersky (@e_kaspersky) February 20, 2015
In certain sense Shodan is like a guy who walks throughout the city and knocks on every door he sees. But instead of doors Shodan “knocks” on every IPv4 address, and instead of some city there is the whole world.
If you ask that guy about a particular type of doors or about doors in a particular part of the city — he certainly would know something and would provide you the information: how many of those doors are there, who answers them and what do they say. Shodan gives you the same information about those IoT items: how are they called, what type are they, and is there a web interface one can use. It’s not totally free — Shodan requires a subscription, which is relatively cheap.
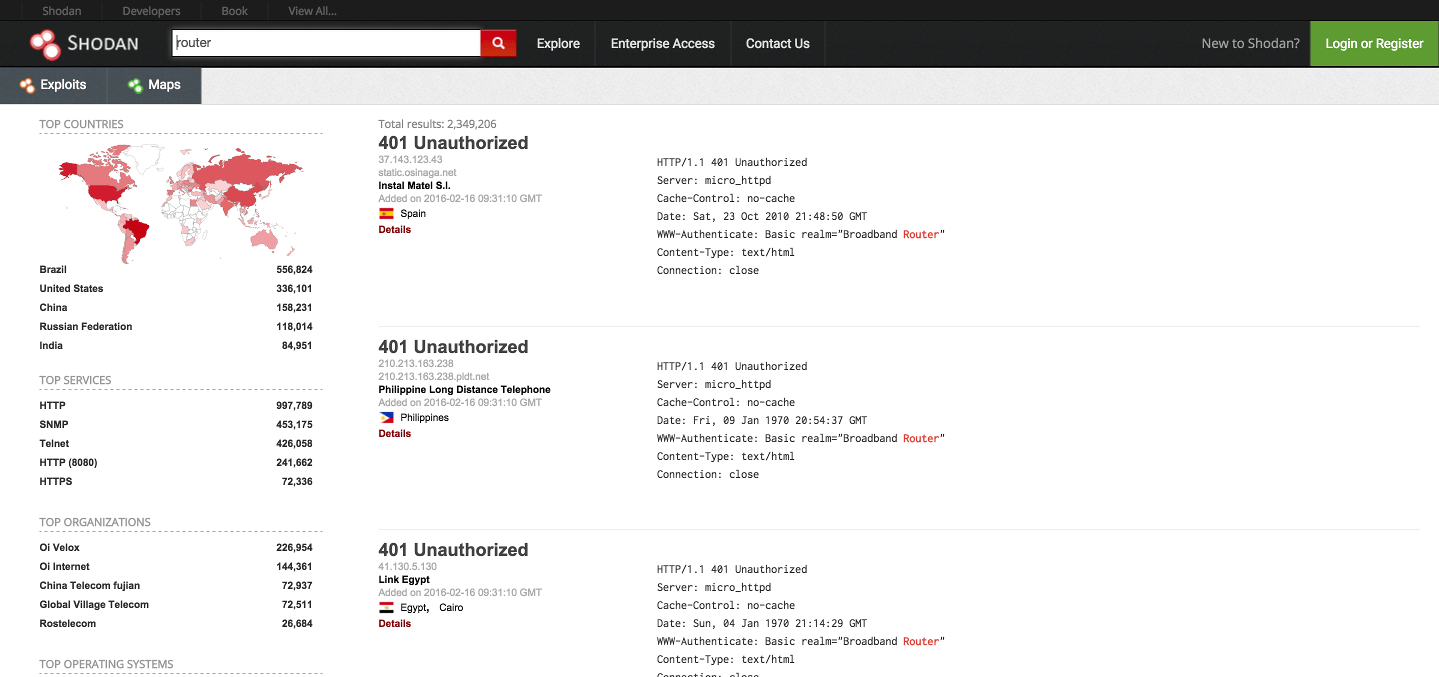
There is no problem on knocking on doors unless you find out that there are a lot of doors with no locks and no one who can stop the bad guys from breaking in. In the world of IoT these doors are represented by unprotected routers, IP cameras and other things that use default logins and passwords. Once you’ve managed to enter their web-interface and figure out the login/password — you can gain full access to them. And it’s not rocket science since the information about default logins and passwords for different connected devices can usually be found on the websites of their manufacturers.
How will the Internet of Things affect cybersecurity? – http://t.co/fWScmf4QfQ pic.twitter.com/sAk1mcZPg5
— Kaspersky Lab (@kaspersky) April 9, 2015
If it’s an IP camera, you can see everything it sees and even control it if it supports something like that. If it’s a router, you can change its settings. If it’s a baby monitor — you can talk to the poor baby in a scary voice. It’s all up to your moral standards.
#parents Is that connected baby monitor exposing your kids to a hacker? Possibly. https://t.co/H2nKD5ck86 pic.twitter.com/jmgJdwuDj5
— Kaspersky Lab (@kaspersky) January 14, 2016
But there are other things that can be found with Shodan — like, for example, an unprotected X-ray machine, which allows you to see the pictures it takes.
Exploring Shodan is rather interesting as many people doing it are curious to know what they can discover. Some have found water park facility controls, while others stumbled upon a nuclear plant. Let’s add car washes, heat pumps, ATMs, and pretty much everything else you can imagine that has an internet connection. Our expert Sergey Lozhkin has stumbled upon some medical equipment, but that’s another story.
The list of exposed medical devices @scotterven found using #Shodan #TheSAS2016 pic.twitter.com/GXNHNsl8mC
— Eugene Kaspersky (@e_kaspersky) February 9, 2016
If an insecure IP camera can only potentially harm someone’s privacy, other insecure connected things like the aforementioned water park facility controls or some onboard train systems are capable of turning a rather big area into a local apocalypse, if they end up operated by the wrong hands. That’s why manufacturers and system administrators of such critical infrastructure have to be extremely careful with the security of these connected things.
For a long time Shodan was the only IoT search engine. In the year 2013 a free rival called Censys emerged (unlike Shodan’s fees). It is also a search engine for the IoT relying on the same basic principles, but, as its creators say, more precise when it comes to searching for vulnerabilities. Oh, yes, Censys can actually give you a list of the devices with a particular vulnerability, for example, those vulnerable to Heartbleed.
Great explanation of the heartbleed bug, from the always amazing @xkcd http://t.co/zVdNQixlaE pic.twitter.com/j5jn9dFD3I
— Josh Long (龙之春) (@starbuxman) May 8, 2014
Censys was created by a group of scientists from the University of Michigan as an instrument to make Internet more secure. In fact, both Shodan and Censys are meant for security researches, but as the duo gains more and more attention, there certainly can be a lot of people who would try to use it for more nefarious purposes.
Neither Shodan nor Censys are likely to be used by some serious cybercriminals — the real big bad guys have had botnets for a while, which can serve the very same purpose yet yield more power. It took Shodan’s creator John Matherly only 5 hours to ping and map all the devices on the whole Internet, and a botnet utilising hundreds of computers would probably do that even faster.
#Shodan shows thousands of exposed ATMs potentially vulnerable to a network attack @_endless_quest_ #TheSAS2016 pic.twitter.com/9E3SSYwG89
— Eugene Kaspersky (@e_kaspersky) February 9, 2016
But there are a lot of other people who already have tried to misuse Shodan and Censys to play bad tricks and pranks on other people. And while the problem with the IoT security is mostly for the manufacturers to solve, there are a few things that you can do about it to secure those connected things that actually belong to you. We’ll have our experts walk you through them in one of our upcoming blogposts in the ‘Internet of Things Search‘ series.
Source: kaspersky.com



