Let’s say that your internet connection suddenly went down or, perhaps, you cannot reach your favorite website. There’s a reason for that; according to our sources, there’s a massive attack against Cisco switches going on right now – these switches are used in data-centers all across the globe.
A bot that hunts for Ciscos
The attack seems to be happening in the following manner. An unknown threat actor is exploiting a vulnerability in a piece of software called Cisco Smart Install Client, which allows them to run arbitrary code on the vulnerable switches. The malefactors then rewrite the Cisco IOS image on the switches and change the configuration file, leaving a message that reads “Do not mess with our elections” there. The switch then becomes unavailable.
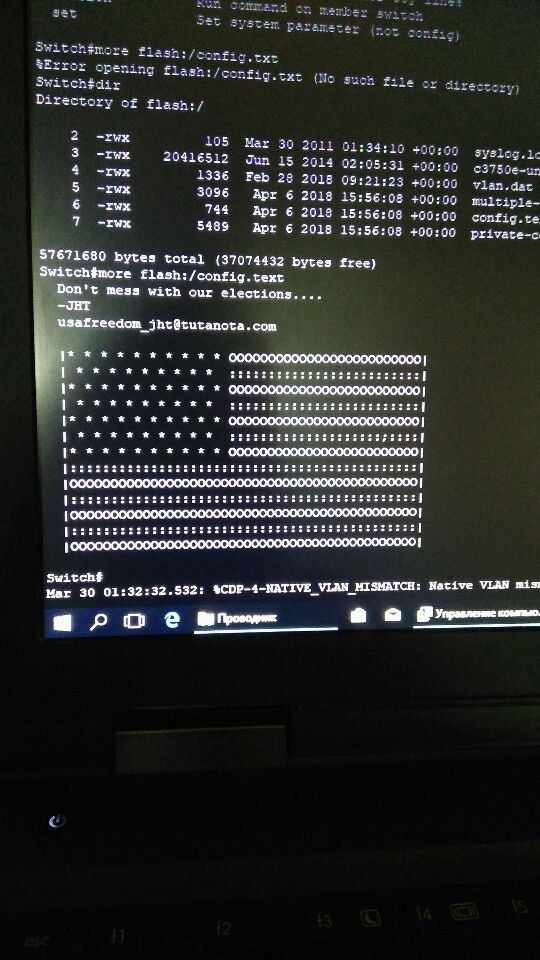
It seems that there’s a bot that is searching for vulnerable Cisco switches via the IoT search engine Shodan and exploiting the vulnerability in them (or, perhaps, it might be using Cisco’s own utility that is designed to search for vulnerable switches). Once it finds a vulnerable switch, it exploits the Smart Install Client, rewrites the config – and thus takes another segment of the Internet down. That results in some data centers being unavailable, and that, in turn, results in some popular sites being down.
According to Cisco Talos, there are more than 168,000 devices found on Shodan, that have this vulnerability. The scale of the attack is yet to be determined, however, it might be really big – with entire Internet-providers and data-centers impacted. It seems that the attack is mostly targeting the Russian-speaking segment of the Internet, yet other segments are clearly more or less affected as well.
We are studying the attack and will add more details to this post once we know them.
For system administrators: how to cope with this
Initially, the Smart Install function was meant to be an instrument for system administrators to make their life easier. It allows remote configuration and OS image-management on Cisco switches. In other words, you can deploy equipment on a remote site and configure everything from the HQ — that’s called Zero Touch Deployment. To make it possible Smart Install Client should be enabled and TCP 4786 port should be opened (both options are enabled by default).
Smart Install protocol does not require authentication by design, that is why it is a question if we can call it a vulnerability. Cisco does not. They call it a misuse of the Smart Install protocol. Actually, it is a problem of datacenters which failed to limit access to TCP 4786 port or to disable Smart Install at all.
To check if Smart Install is working you can run the “show vstack config” command on your switch. If the switch responds positively, which means that Smart Install is enabled, it’s better to disable it with the no vstack command.
However in some releases of Cisco operating system it will work only until the switch is rebooted (in Cisco Catalyst 4500 and 4500-X Series Switches with 3.9.2E/15.2(5)E2 system; in Cisco Catalyst 6500 Series Switches with system versions 15.1(2)SY11, 15.2(1)SY5, and 15.2(2)SY3; in Cisco Industrial Ethernet 4000 Series Switches with 15.2(5)E2 and 15.2(5)E2a systems; and in Cisco ME 3400 and ME 3400E Series Ethernet Access Switches with OS 12.2(60)EZ11). In that case you are advised to upgrade (or maybe even downgrade) the system version or automate running of the “no vstack” command. To detect the version of the operating system in use you can run a “show version” command.
If your business-processes do not allow to shut down Smart Install, or version of your Cisco OS do not support “no vstack” command (and it is quite possible — it was added with one of the patches), then you should limit connections to port 4786. Cisco recommends doing that with Interface Access Control Lists, so that only authorized equipment could connect to your switches via that port. In the example below this equipment is placed on 10.10.10.1 IP address.
Example:
ip access-list extended SMI_HARDENING_LIST
permit tcp host 10.10.10.1 host 10.10.10.200 eq 4786
deny tcp any any eq 4786
permit ip any any
To learn more about this problem you can read about Cisco Smart Install Protocol Misuse here.
Source: kaspersky.com




