If you’ve ever mistyped a website URL — a double or missing letter, amazom for amazon — and ended up on some strange website, you may have fallen victim to an old but effective trick: typosquatting, which is also sometimes called URL hijacking. For various reason people buy domains that resemble those of legitimate websites to lure Internet users to their pages. And sometimes these people are cybercriminals and the reason is spreading malware.

Typosquatting is a nuisance for businesses, and some have even brought court cases to combat it. Of course, it’s also a threat for consumers, who may find themselves looking at unwanted spam sites, or worse, infected by malware. Before we look at an example, we should point out that as part of our efforts to reduce the number of victims of malware infection, when we find a compromised website, we always try to alert its administrator.
A real-world example
The following is the WHOIS information of a website we encountered that unintentionally hosts malware. In the “Administrative Contact” field, you will see the string “A***3JP”. That’s a JPNIC handle managed by Japan Registry Service (JPRS), which is a key to figuring out who is the administrator of the site. (In other cases, e-mail addresses are registered in this field.)
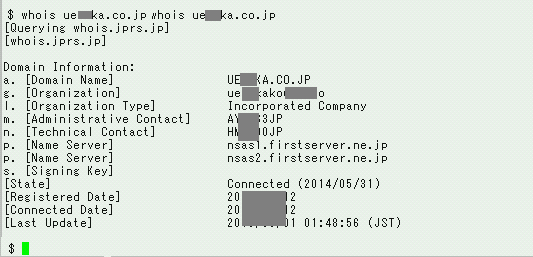
We checked who administers the “A***3JP” domain:
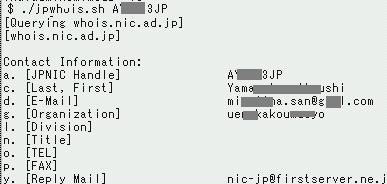
The e-mail address in the “E-Mail” field is the contact information for the person who should be made aware of the malware infection on his/her website. Alerting administrators who are unaware of infections is one of the important steps in the process of preventing malware from spreading further.
Taking a closer look, however, we found a flaw in the address. It looks like a Gmail address, but actually it is not. A letter is missing.
For some countries, having correct registration of domain information is a legal obligation. However, in Japan, sometimes registered information is not correct, and what’s worse is that errors may be intentional. In any case, without the right e-mail address, we are unable to alert the site administrator.
In this case, however, the intention of the Gmail-like domain was clear.
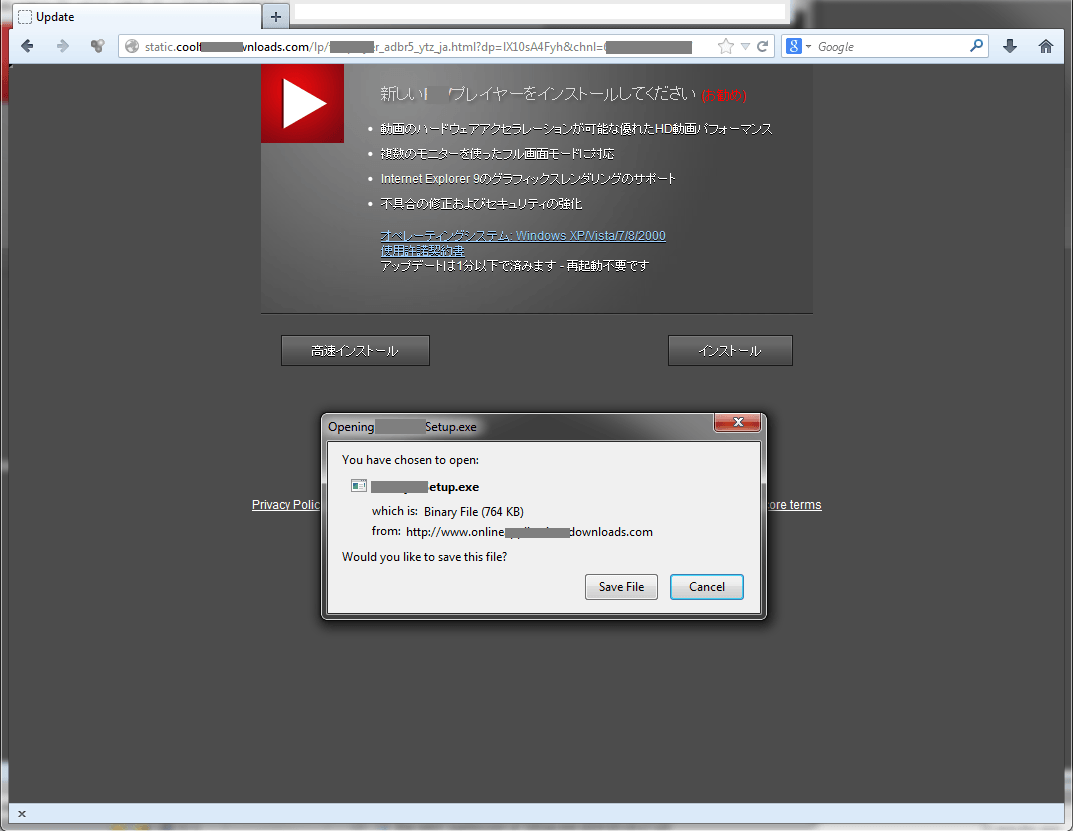
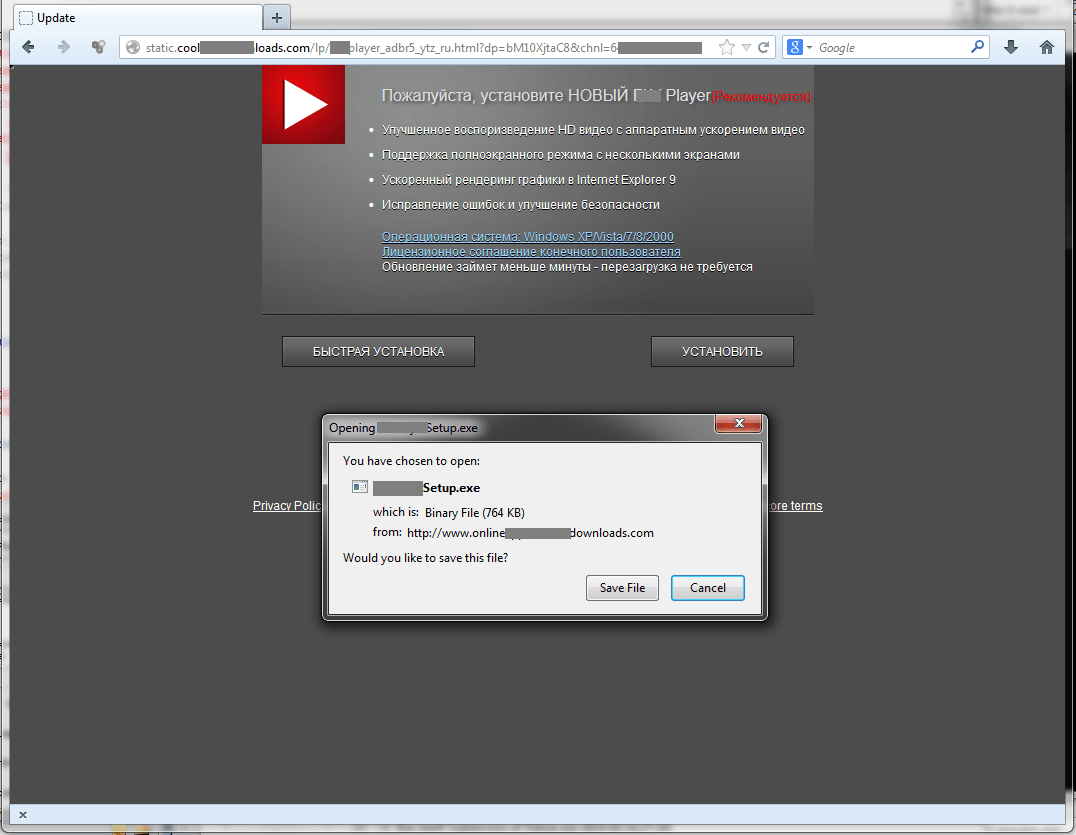
The website could be displayed in various languages depending on a visitor’s language environment, including Japanese, German, Spanish, Italian, Dutch, Polish, Portuguese, Russian, Swedish, and Turkish, but not English. As you can see from the sample screenshots of the website, its legitimate look could easily trick accidental visitors into downloading and installing the object.
Japanese:
Russian:
Typosquatting is not actually new; it’s been around for a while. Despite the method being well known, its victims continue to increase worldwide. To avoid being a victim of typosquatting-driven malware, try to slow down and take care when typing URLs. Most important, regularly update your OS and security software — that way you’ll be much less likely to get into trouble even if you mistype a website address.
Source: kaspersky.com




