Some time ago, an antivirus expert from our Global Research and Analysis Team, David Jacoby, discovered multiplatform malware that was distributed through Facebook Messenger. A few years ago, similar outbreaks were occurring quite often, but none have appeared lately; Facebook was doing a lot to prevent similar attacks.
First a preliminary report was published. At that time, Jacoby still had not had enough time to research many details about how the malware operated, but now he has, and we are ready to share them. From a user’s perspective, here’s how the infection progressed.
- The user received a message in Facebook Messenger from a friend. The message contained the word “Video,” the name of the sender, a random smiley, and a short link. It might look like this, for example:
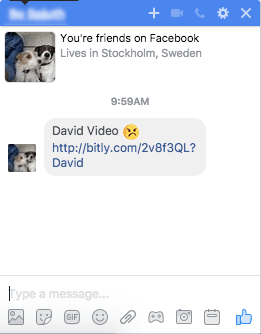
- The link redirected to Google Drive, where the user saw something resembling a video player with a picture of the original sender in the background and what looked like a Play button.
- If the victim attempted to play back the “video” in Google Chrome, they were redirected to a page that looked much like a YouTube page and offered to install an extension for Chrome.
- If the user agreed to the installation, then the extension began to send out malicious links to their friends — and everything followed the same algorithm for each of them over again.
- Users of other browsers were persistently reminded to update their Adobe Flash Player instead of being offered the extension. The file they downloaded turned out to be adware — essentially, malefactors used advertisements to earn their money.
Jacoby, along with Frans Rosen, a researcher with whom he has been working on a project called “Hunting bugs for humanity,” have analyzed this malicious campaign and worked out how it operates.
The page that users were redirected to after following the link in Facebook Messenger was basically a PDF file that had been published to Google Drive. It opened as a preview. The file had a picture from a user’s Facebook page — the user whose identity was used to spread the malware — an icon for playing back the video shown over the picture, and the link that the victim opened by trying to click the playback button.
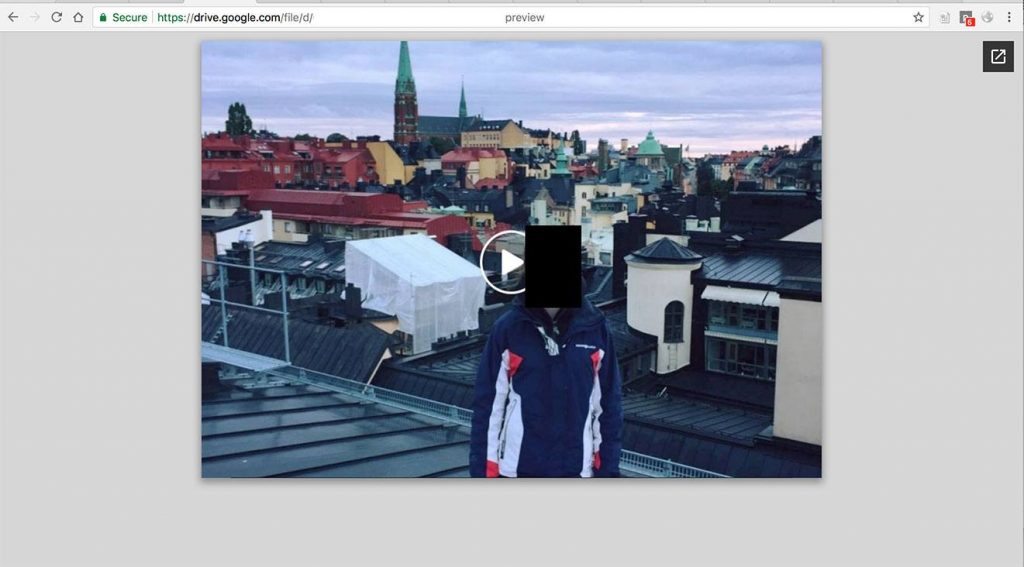
Clicking the link led friends of the victim to this page.
The link caused several redirections, landing the user on one of several websites. Victims using browsers other than Google Chrome ended up on a website offering to download adware masked as an update for Adobe Flash Player.
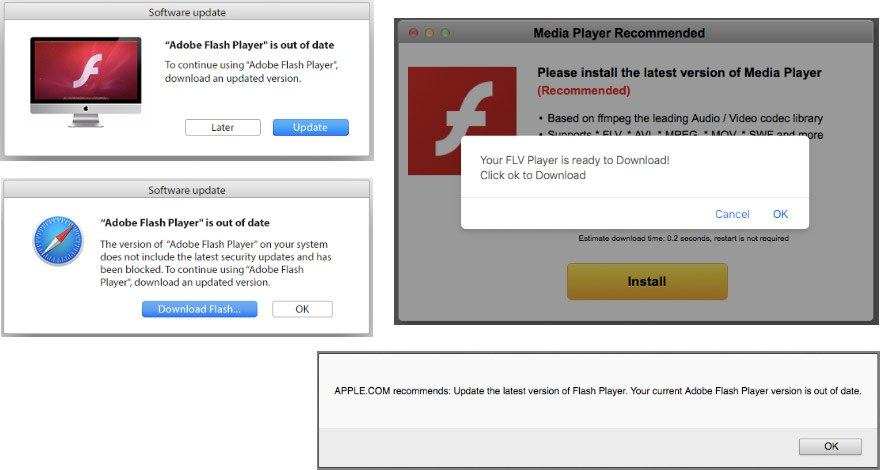
Browsers other than Google Chrome offered to download adware disguised as Adobe Flash Player.
In the case of Chrome, that was just the beginning: If the victim agreed to install the extension offered on the landing page, it began monitoring what websites the user opened. As soon as the victim navigated to Facebook, the extension stole their login credentials and the access token and sent them to the malefactors’ server.
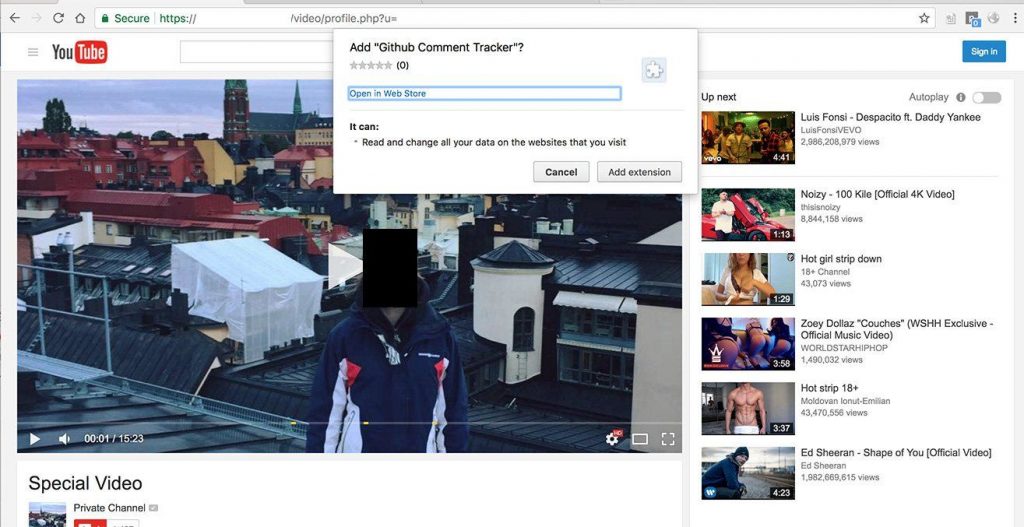
A fake YouTube page offering to install Google Chrome extensions.
The crooks had found an interesting bug in Facebook. As it turned out, the unsecure Facebook Query Language (FQL), which was disabled a year ago, was not completely wiped out; it was blocked for applications, but with a few exceptions. For example, Facebook Pages Manager, an iOS application, still uses FQL. Thus, to gain access to the “locked out” feature, malware simply has to act on behalf of the application.
By using the stolen credentials and accessing the obsolete Facebook feature, the crooks could request that the social network send them the contact list of the victim, cull those who were not currently online, and randomly select 50 new victims from the remainder. Then, those users were bulk-messaged with a new link to Google Drive with a PDF file preview generated with the picture of the person on whose behalf the new messaging wave commenced. All in all, a vicious cycle.
It is worth noting that among other things, the malicious script “liked” a specific Facebook page, apparently to collect statistics for the infection. In the course of the attack, Jacoby and Rosen observed, the malefactors changed several of the specific pages, possibly as Facebook closed the previous ones. Judging by the number of “likes,” there were tens of thousands of victims.
One of the pages that infected users “liked.”
Their analysis of the code revealed that the malefactors were initially planning to use localized messages but then changed their minds and resorted to the short and simple “Video.” The localization function‘s code showed that the crooks were primarily interested in Facebook users from several European countries such as Turkey, Italy, Germany, Portugal, France (also, francophone Canada), Poland, Greece, Sweden, and all countries with English-speaking users.
The mutual effort of several companies has put an end to the infection’s spread for now. Nonetheless, this story is a great reminder that extensions for browsers are not as harmless as they may seem. To stay safe and not fall victim to similar malicious campaigns, avoid installing browser extensions without absolute confidence that they are safe, that they will not steal your data, and that they won’t track your online activities.
Also, clicking every link, even links that seem to be from someone you know, is out of the question. It is always a good idea to make sure that it is really your friend on the other end of the line, not some criminal who took control of your friend’s account.
Source: kaspersky.com



