Scam artists know no bounds—and that also applies to stealing your cryptocurrency. Crypto scams are like any other financial scam, except the scammers are after your crypto assets rather than your cash.
Crypto scammers use many tactics in other financial crimes, such as pump-and-dump scams that lure investors to purchase an asset with fake claims about its value or outright attempts to steal digital assets.
This time scammers were trying to get an investor to send a digital asset as a form of payment for a fraudulent transaction.
It starts with a Tweet used as bait to lure innocent cryptocurrency investors into purchasing a non-existent token, related to a reputed company, SpaceX.
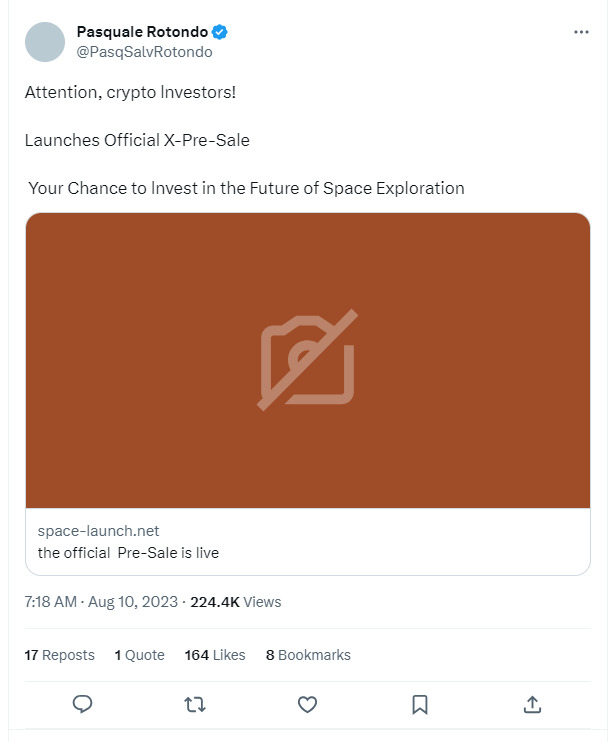
The theme used here by scammers is the sale of the official cryptocurrency of SpaceX. In the above image we can also see the reach of the tweet is high. (224.4K views)
Protection with McAfee+:
McAfee+ provides all-in-one online protection for your identity, privacy, and security. With McAfee+, you’ll feel safer online because you’ll have the tools, guidance, and support to take the steps to be safer online. McAfee protects against these types of scam sites with Web Advisor protection that detects malicious websites.
The link present in this tweet redirects to space[-]launch[.]net, which is already marked as malicious by McAfee.
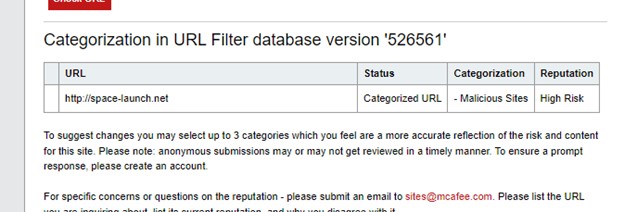
A WHOIS search on the site reveals it is hosted on Cloudflare. Cloudflare has increasingly become the number one choice for scammers to host malicious websites and protect their assets.
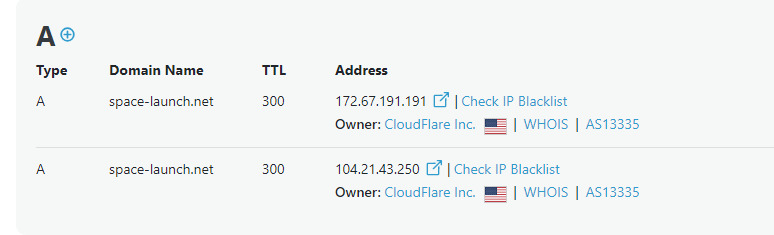
A WHOIS lookup on the domain reveals redacted personal information. No surprises there
When we click on the link, it takes us to a login page and asks for SpaceX login credentials. This page was designed as a phishing page for people who have real SpaceX login credentials.
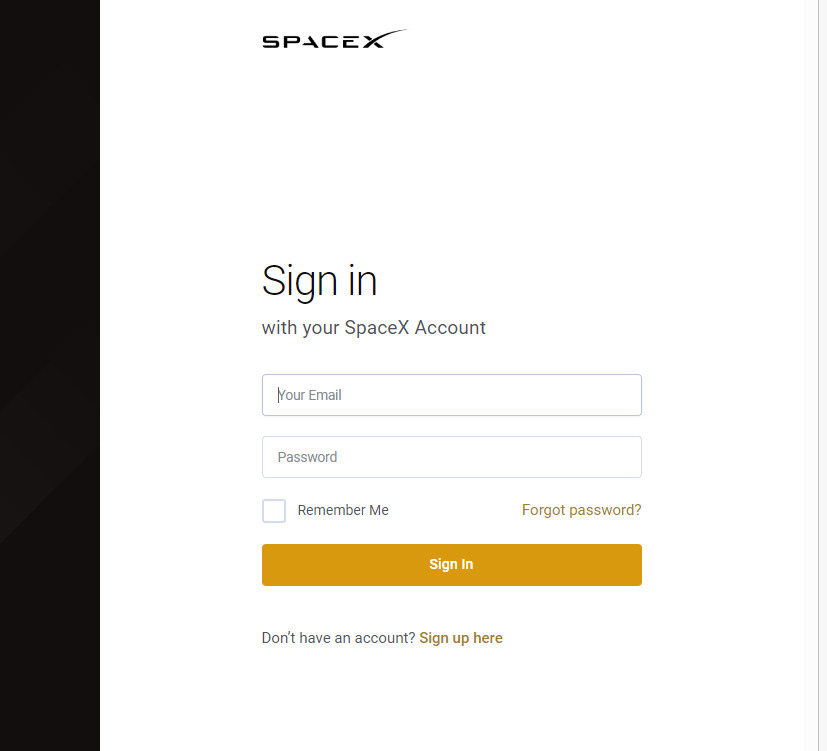
For people who don’t have SpaceX credentials, they can use the signup link.
After we log in, it redirects to a landing page where one can purchase the supposedly original cryptocurrency launched by SpaceX
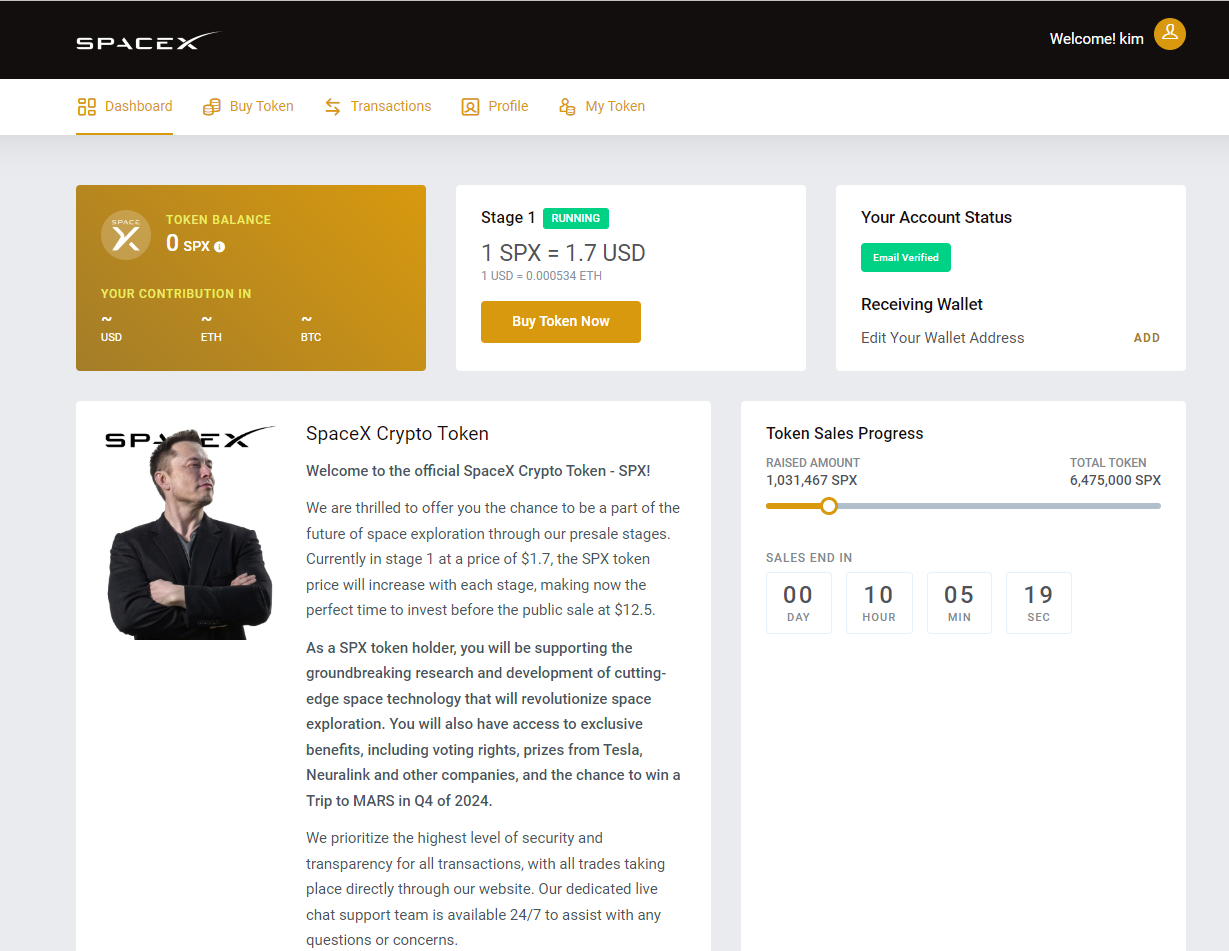
As you can see, it impersonates as the official SpaceX portal for buying their token. It also has all the elements related to SpaceX and its branding.
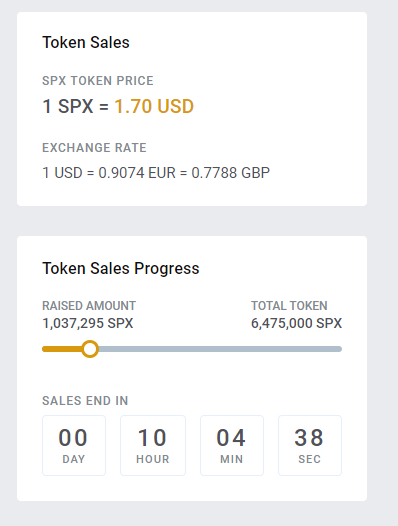
In the above picture, we can see that scammers are employing the social engineering trick of FOMO (Fear Of Missing Out) as they have created a timer showing that the fake tokens are only available for purchase for the next 10 hours. This also makes sure that the scam would end before all the online security vendors flag the site.
Scammers also allow users to purchase fake tokens from about 22 cryptocurrencies, the prominent being Bitcoin, Ethereum, and USDT.
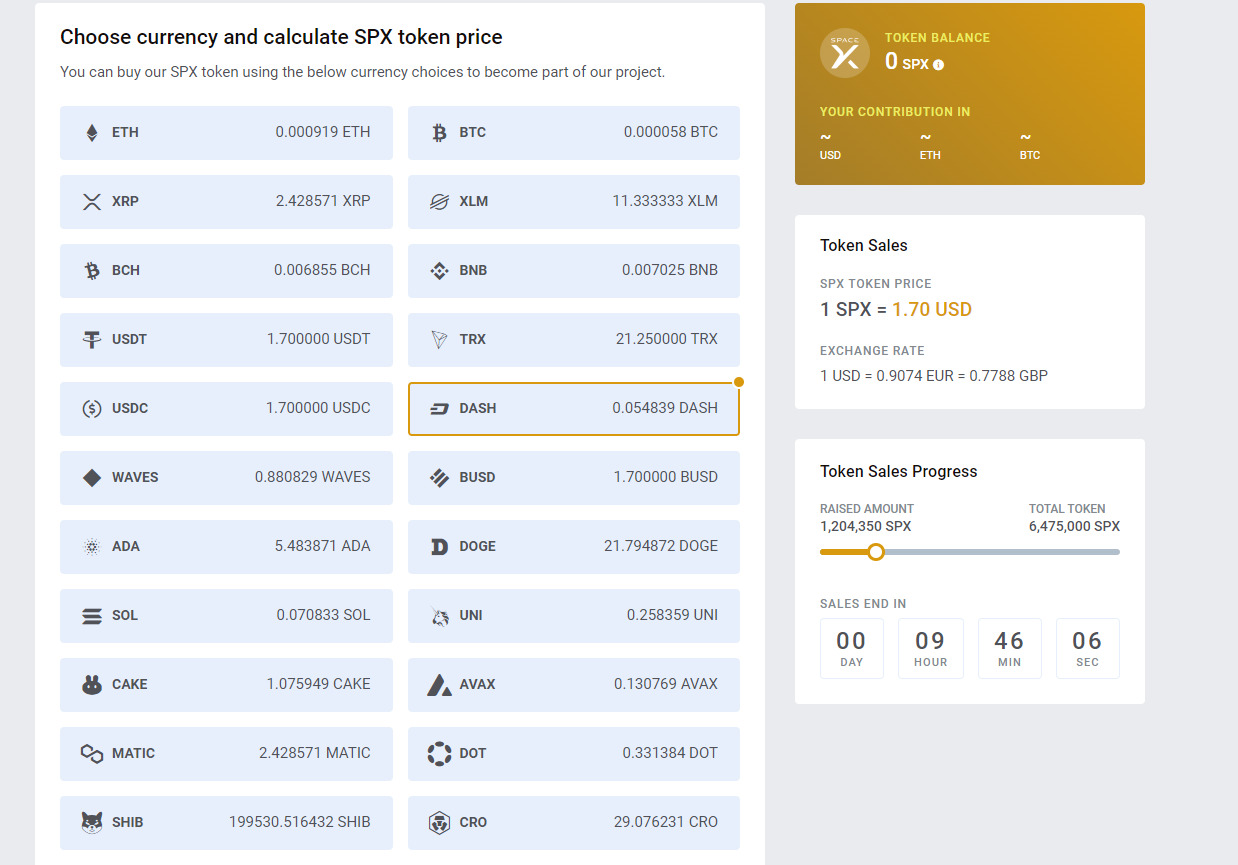
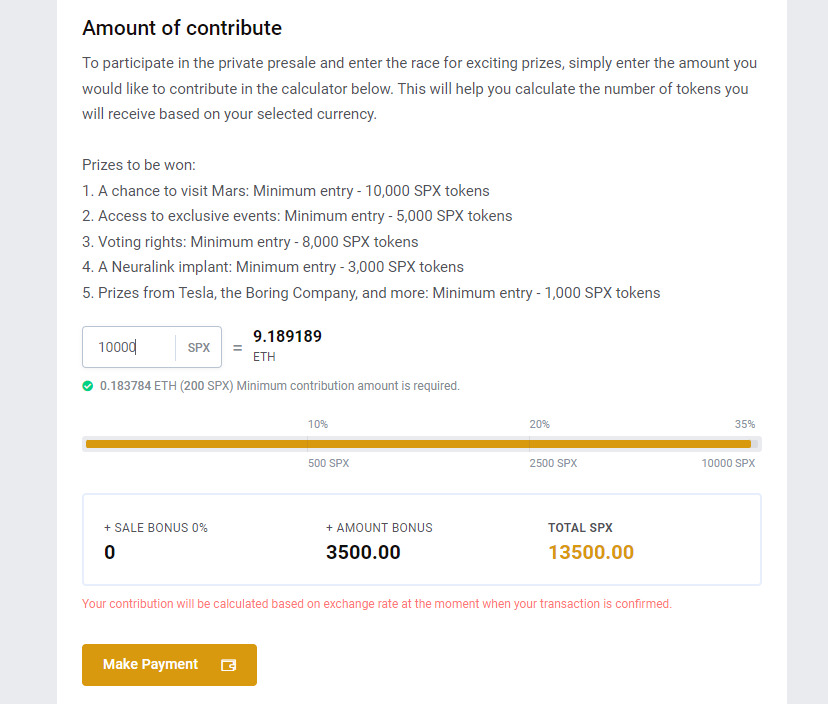
Scammers even offer a bonus of fake SpaceX tokens if users are ready to purchase a minimum amount
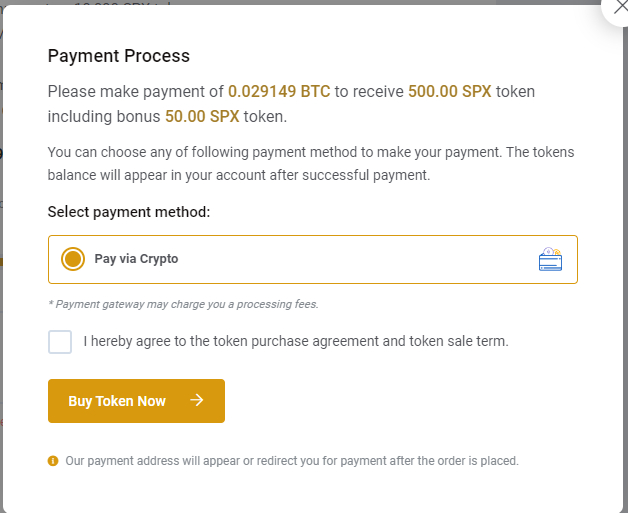
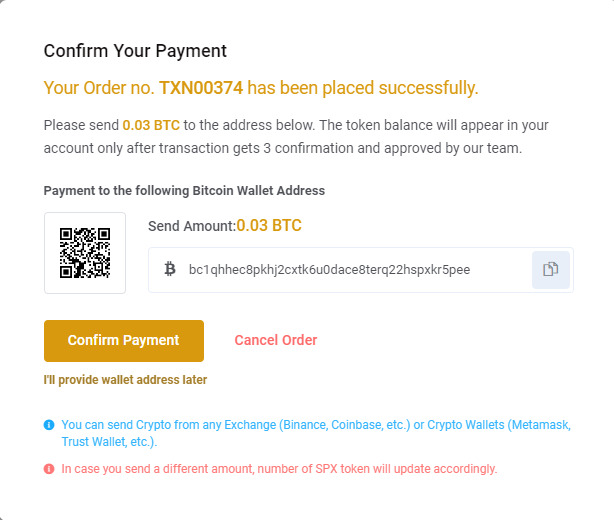
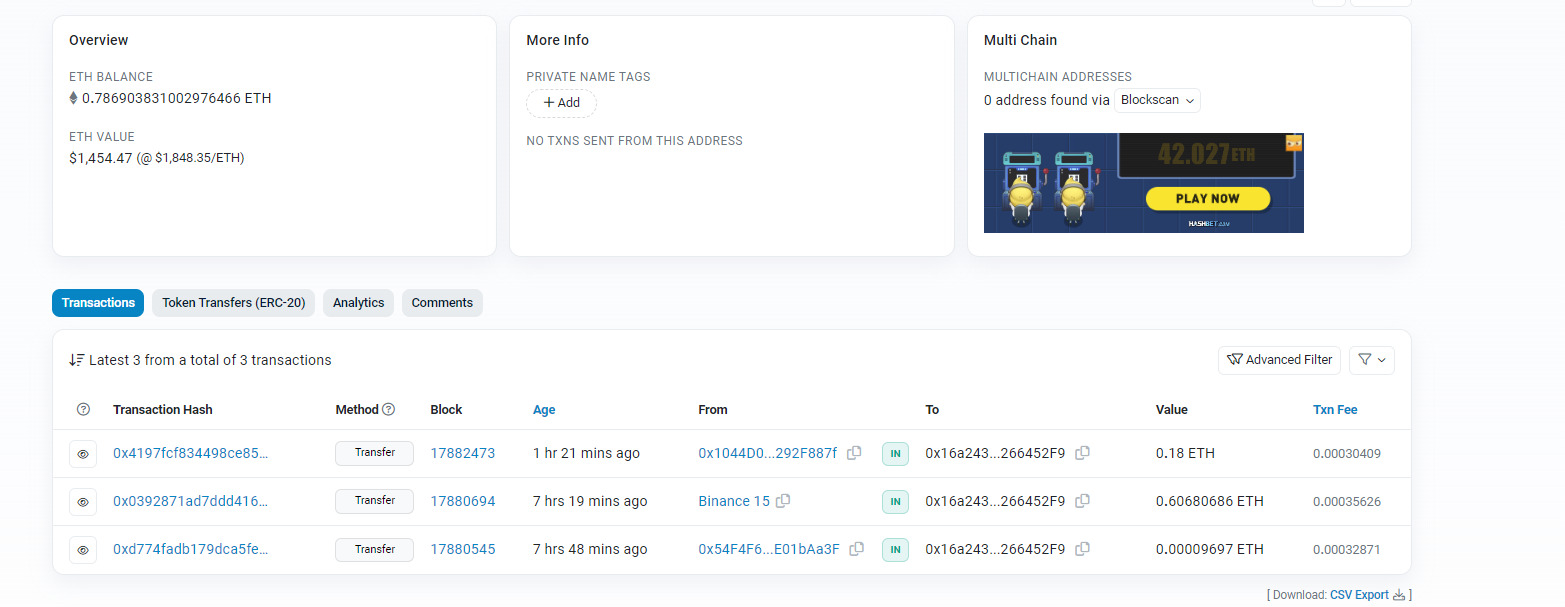
Here we can find the BTC wallet address of the scammers and see the transactions related to these wallets.
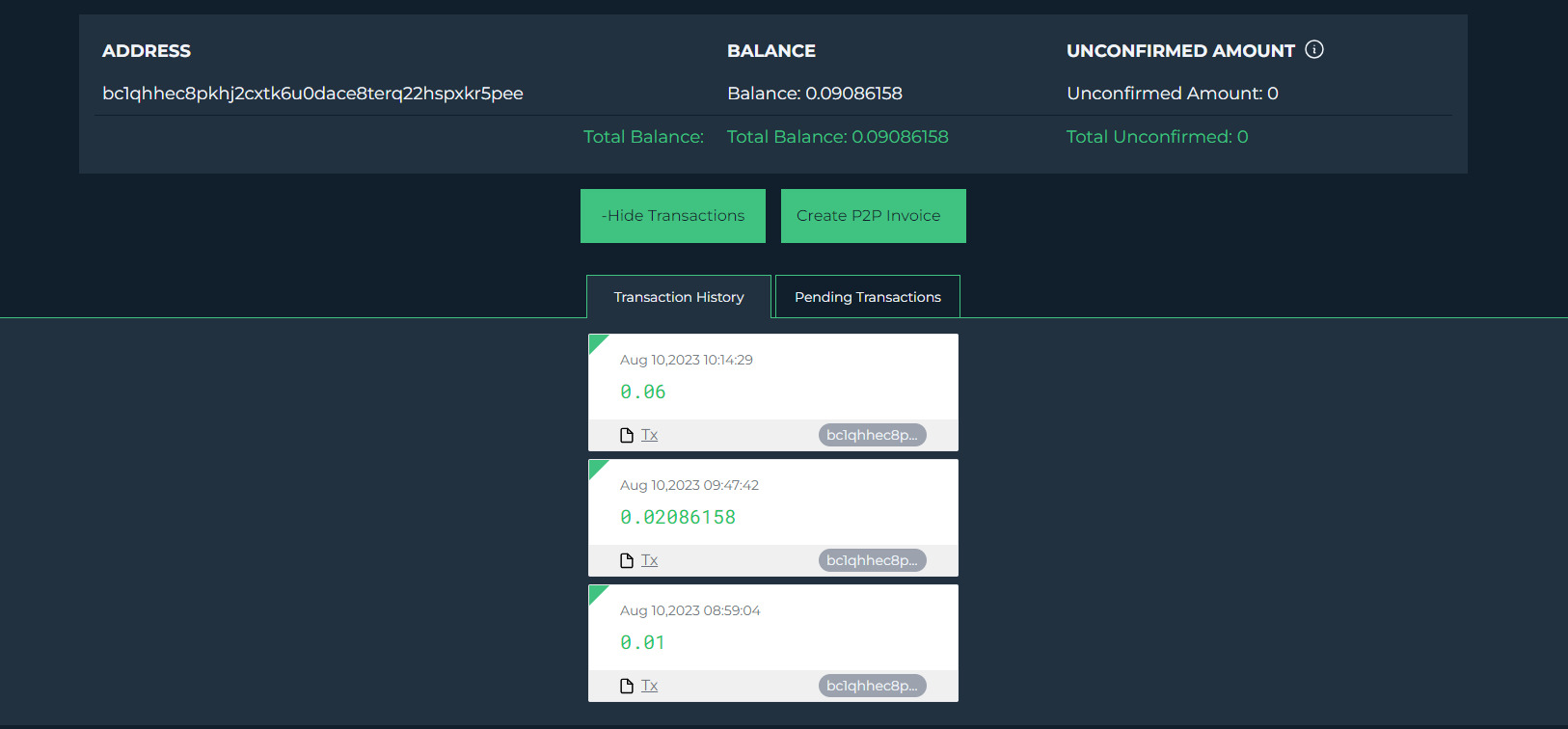
The crypto wallet addresses of scammers for the following currencies are.
- BTC bc1qhhec8pkhj2cxtk6u0dace8terq22hspxkr5pee
- USDT 398a9BF5fe5fc6CaBB4a8Be8B428138BC7356EC1
- ETH 16a243E3392Ffd9A872F3fD90dE79Fe7266452F9
Looking at transactions related to these addresses, we find people have become victims of this scam by sending payments to these wallets. The Bitcoin wallet above has gathered around 2,780 US dollars. You can also see three of the last transactions made to the account.
Similarly, for Ethereum, the scammers have gathered around 1,450 US dollars
We observed two popular cryptocurrencies, but scammers are using about 22 different crypto wallets.
Crypto phishing scams constantly evolve, and new tactics emerge regularly. Users should take the initiative to educate themselves about the latest phishing techniques and scams targeting the cryptocurrency community. Also, stay informed by researching and reading about recent phishing incidents and security best practices.
IOC (Indicator of Compromise)
| Domain | Crypto Type | Wallet address |
| space[-]launch[.]net | BTC | bc1qhhec8pkhj2cxtk6u0dace8terq22hspxkr5pee |
| space[-]launch[.]net | USDT | 398a9BF5fe5fc6CaBB4a8Be8B428138BC7356EC1 |
| space[-]launch[.]net | ETH | 16a243E3392Ffd9A872F3fD90dE79Fe7266452F9 |
| space[-]launch[.]net | XRP | rnmj4xsaaEaGvFbrsg3wCR6Hp2ZvgjMizF |
| space[-]launch[.]net | DASH | XxD3tJ7RA81mZffKFiycASMiDsUdqjLFD1 |
| space[-]launch[.]net | BCH | qr45csehwfm5uu9xu4mqpptsvde46t8ztqkzjlww68 |
| space[-]launch[.]net | USDC | 0x398a9BF5fe5fc6CaBB4a8Be8B428138BC7356EC1 |
source: McAfee Labs



