The place: Moscow, Russia. The time: Five minutes into the Russia–Spain World Cup match. Scene: Having just entered a bar to cheer on the guys, I had my iPhone stolen.
This story wouldn’t be worth a blog mention, were it not for the clever iPhone-stealing tricks employed by the scammers.
Here’s how it played out:
- 5:00: The match kicks off.
- 5:01: I enter a crowded bar in the center of Moscow hoping to find a space, all the while clutching my iPhone; I had to let my friend know where she could find me.
- 5:07: My boyfriend asks me to call my friend, whereupon I realize with horror that I’m phoneless.
My first reaction was to call my phone from a different device. No luck — the ringing cut off after a few seconds. Then it hit me that my iPhone wasn’t just lost; it was stolen. I had no idea how that could have happened: I thought I’d been holding it the whole time, but perhaps I put it in my pocket for a couple of minutes unconsciously. My next move was to look for security and get to know the police officer on duty in the bar. Then a happy thought hit me: the Find My iPhone app — I just needed to enable Lost Mode and trace the missing device.
If someone steals your PIN-locked iPhone, all they can really do is demand ransom for it or sell it for parts. To resell the iPhone as a unit, it must be unlocked. In the case of my iPhone X, that would require either my face or my PIN. What’s more, after several unsuccessful unlock attempts, the iPhone doesn’t allow any more tries for an hour — and after several more, it effectively turns into a pumpkin, Cinderella-style. That’s how Apple does security.
If your iPhone is lost or stolen, the Find My iPhone app helps you get it back. The app is handy because you can use it to lock the device and enable Lost Mode with the message: This iPhone has been lost. Please call me. [phone number] Not only that, you can see the phone on a map (if it wasn’t turned off). We used the app — maybe the attacker would want to ransom the phone or be stupid enough to turn it on?
Psychological phishing
That’s when things started to get interesting. An hour later, the following message was sent to the number specified in my Lost Mode lock-screen note.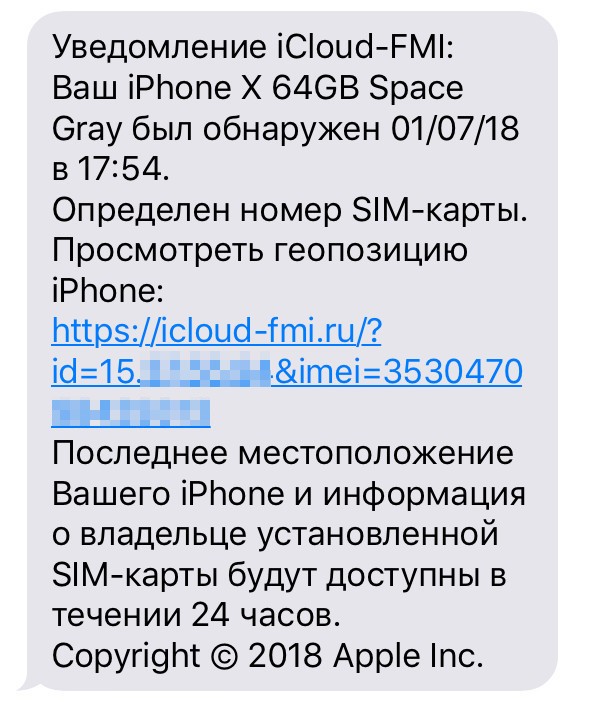
iCloud FMI notification: Your iPhone X 64GB Space Gray was located on July 01, 2018 at 17:54. The SIM card number has been identified. Follow the link to view the iPhone’s geolocation. The most recent location of your iPhone and information about the owner of the installed SIM card will be available within 24 hours. Copyright 2018 Apple Inc.
Take a close look. Anything strikes you as odd? A few things should: The site URL isn’t an official one; companies don’t usually mention copyright in an SMS message; and, come to think of it, why would Apple send a text instead of a notification in the Find My iPhone app? In other words, it’s phishing, but rather skillfully done. The cybercriminals clearly know what they are doing: The message is sent right when the victim is frantically trying to recover the lost device, stressed and psychologically vulnerable.
I’ll admit it: That’s how I was feeling. Yes, I work at Kaspersky Lab, and phishing incidents are routine for me. Yes, I write every day about the latest cybertricks and scams. But at that moment I was panicked and grasping at any opportunity to get my phone back, not really thinking about what I was doing. When the ill-fated SMS arrived on my boyfriend’s phone (his was the contact number specified), we were at the police station. A report was already filed, and the police were ready to help. If I could give them information about the phone’s location, that would greatly improve our chances of getting it back.
So I tapped the link without thinking, saw the familiar iCloud interface, and entered my login and password. The first attempt produced an incorrect password message. I tried again, no luck. The password was etched in my brain, and there was no way I could have made a mistake twice.
I went back to the Find My iPhone app, logged into my account without any trouble, and…my phone wasn’t there. It had simply vanished from the map and the list of devices. Then I took another look at the incoming message and realized what had happened.
The phishing SMS had lured me onto a fake iCloud site, where I had handed my credentials to the cybercriminals. Armed with this data, they had immediately disabled the search function on my device. Through iCloud, they could also erase all of the information on it (all they needed were the iCloud login and password I had just given them). After a hard reset, they would have a practically clean iPhone X that could be assigned a new PIN and resold for a tidy sum.
Of course, I changed my iCloud password immediately, but it was too late. I had lost both my phone and any hope of retrieving it. According to Apple support, the Find My iPhone app is the only way to trace a missing gadget, and if it’s disabled, the device ain’t coming back.
What could have saved me?
- Obviously, if I hadn’t clicked on the phishing link or hadn’t entered my credentials, the scheme would not have worked. But, as my case shows, no one is immune: I know about all kinds of fraud, yet I swallowed the bait.
- Two-factor authentication for iCloud would have saved me even if I had fallen for the phishing trick. Yes, I’d still have given the scammers my login and password, but they would not have been able to use them — they’d have needed another of my devices to receive the authentication code. The moral of the story: Enable two-factor authentication everywhere you can.
Source: kaspersky.com



