Anyone who has an account on any social network or online service is bound to have come across two-factor authentication (2FA) before. It also goes by the name two-step authentication or two-step verification, but the concept’s the same.
But have you ever wondered what it exactly is, how it works and – most importantly – why it’s needed? If so, you’ve come to the right place. We’ll try to answer these questions and more in this post.
What is two-factor authentication?
We’ll begin with a simple definition. When several methods are used simultaneously to validate access rights — that is, for authentication — it’s known as multi-factor authentication.
Most often digital services use two-factor authentication. There’s nothing wrong with using more factors, but the number is usually limited to two so as not to overly irritate users.
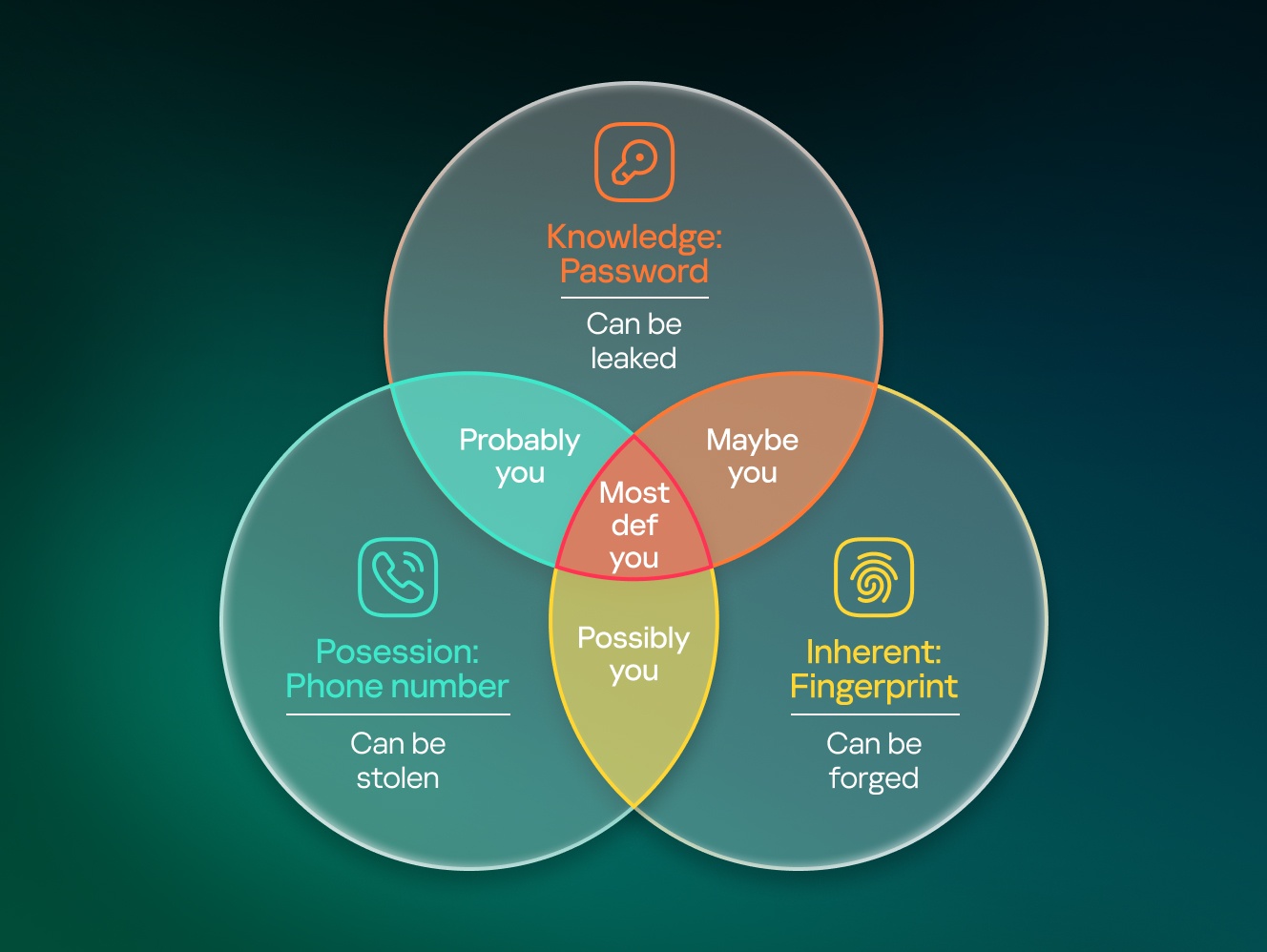
In other words, 2FA provides the optimal balance between account protection and convenient login. But what “factors” can be used to confirm the user’s authentication rights? Here are the most popular options:
- Knowledge. Authentication is granted if you have the correct password, passphrase, numeric code, graphic pattern, answer to a secret question, etc.
- Possession. If you have a certain item (for example, a key, USB token, phone, bank card), this is validation of your access rights. This also includes having access to a phone number or some other account (say, an email), which can be demonstrated, for example, by getting a one-time code.
- Inherent property. It’s often possible to authenticate with some inherent, unique property of the actual user: a fingerprint, voice, face, DNA, iris pattern, characteristic typing style on keyboard, etc.
- Geolocation. Here, authentication is based on the user being in a certain place; for example, if logging in to corporate resources — inside the company’s office.
Note that for multi-factor authentication to work, the methods used to validate the user’s rights must be different. So, if a service asks the user to enter two passwords instead of one (or, say, a password and the answer to a secret question), this cannot be considered 2FA, since the same method of validation (knowledge) is used twice.
Why do you need two-factor authentication?
Multi-factor authentication is recommended since, individually, each validation method has its own weaknesses. For example, knowledge of some information could be a reliable method — but only if this information is known to the user alone and could in no way somehow be obtained from any other source. But that’s hardly ever the case: the user has to type in a password that’s then transmitted over the internet. Also, they probably store it somewhere since no one can remember all passwords for all accounts. This provides many opportunities for interception and theft.
What’s more, the password is bound to be stored on the side of the online service, from where it could one day leak. And if you use the same password for multiple services (unfortunately, many people still do), then all these accounts are at risk of being hacked.
The same goes for other validation methods. The possession factor isn’t ideal, because your item (key, phone, bank card) might get stolen. Geolocation by itself confirms nothing: there are sure to be many other folks at roughly the same point in time and space as you (unless you happen to be drifting on an ice floe in the middle of the Arctic Ocean).
Perhaps only an inherent property factor can be considered more or less reliable, which is why it’s sometimes used as the sole authentication factor. But there are a fair number of nuances too.
Hence the concept of multi-factor authentication: the greater the number of different factors, the more likely it is that a person who’s trying to get access to the account actually has the right to do so.
Using more factors helps ensure your account will be accessed by you and you alone
So, two-factor authentication is a good idea for a simple reason: to let the service know that you are you, and to make your account harder to hack.
How to use two-factor authentication
We’ll look at the various kinds of 2FA in a separate post; in the meantime, we’ll end this one with a few tips:
- Be sure to enable two-factor authentication for all services that offer it.
- Where possible, select one-time codes from an authenticator app as the 2FA method. And for really valuable accounts, use a FIDO U2F hardware key.
- If the above options aren’t available, any other method will still be far better than having no second factor at all.
- Remember that 2FA doesn’t guard against high-quality phishing (with the exception of FIDO U2F keys), so each time before entering a code, make sure you’re on the real website — not a fake one.
- Use a reliable security solution with built-in anti-phishing protection, such as Kaspersky Premium.
As for creating strong passwords and storing them securely, we recommend Kaspersky Password Manager — the full version of which comes with a Kaspersky Premium subscription. Incidentally, our password manager has several other useful features that will help protect your accounts from hacking.
Source: kaspersky.com



