This blog post is about the UpdraftPlus plugin vulnerability. If you’re a UpdraftPlus user, please update the plugin to at least version 1.23.4.
Patchstack paid plan users are protected from the vulnerability. You can also sign up for the Patchstack Community plan to be notified about vulnerabilities as soon as they become disclosed.
For plugin developers, we have security audit services and Threat Intelligence Feed API for hosting companies.
About the UpdraftPlus WordPress plugin
The plugin UpdraftPlus (versions 1.23.3 and below, free version), which has over 3+ million active installations are known as one of the most popular backup plugins in WordPress.

This plugin is a WordPress plugin which allows us to simplifies backups and restoration. We could perform backup into the cloud directly like Dropbox, Google Drive, Amazon S3 (or compatible), UpdraftVault, Rackspace Cloud, FTP, DreamObjects, Openstack Swift, and email.
The security vulnerability in UpdraftPlus
This plugin suffers from CSRF vulnerability that could lead to a stored site wide XSS on the wp-admin area. This vulnerability allows any unauthenticated user from stealing sensitive information to, in this case, privilege escalation on the WordPress site by tricking privileged user to visit the crafted malicious targeted WordPress site URL. The described vulnerability was fixed in version 1.23.4 and assigned CVE-2023-32960.
Find out more from the Patchstack database
The underlying XSS vulnerable code located on build_authentication_link function which will build and return the authentication link for certain backup method :
public function build_authentication_link($instance_id, $text) {
$id=$this->get_id();
return ' '.$text.'';
}The $instance_id variable is directly constructed as HTML without proper sanitization. Above function could be called from get_authentication_link function that will either return or echo the constructed auth link for the remote storage method :
public function get_authentication_link($echo_instead_of_return=true, $template_instead_of_notice=true) {
if (!$echo_instead_of_return) {
ob_start();
}
$account_warning='';
$description=$this->get_description();
if ($this->output_account_warning()) {
$account_warning=__('Ensure you are logged into the correct account before continuing.', 'updraftplus');
}
if ($template_instead_of_notice) {
$instance_id="{{instance_id}}";
$text=sprintf(__("After you have saved your settings (by clicking 'Save Changes' below), then come back here and follow this link to complete authentication with %s.", 'updraftplus'), $description);
} else {
$instance_id=$this->get_instance_id();
$text=sprintf(__('Follow this link to authorize access to your %s account (you will not be able to backup to %s without it).', 'updraftplus'), $description, $description);
}
echo $account_warning . ' ' . $this->build_authentication_link($instance_id, $text);
if (!$echo_instead_of_return) {
return ob_get_clean();
}
}Notice that the value returned from build_authentication_link function will be directly echoed and could turns into XSS if we could fully control the $instance_id variable. The $instance_id variable in that function, could be fetched from $this->get_instance_id() function which act as a getter to the $this->_instance_id variable that will be set from set_instance_id function :
/**
* Sets the instance ID - for supporting multi_options
*
* @param String $instance_id - the instance ID
*/
public function set_instance_id($instance_id) {
$this->_instance_id=$instance_id;
}
/**
* Sets the instance ID - for supporting multi_options
*
* @returns String the instance ID
*/
public function get_instance_id() {
return $this->_instance_id;
}The set_instance_id function could be called from do_authenticate_storage function which will reset any saved options and start the bootstrap process for an authentication :
public function do_authenticate_storage($instance_id) {
try {
// Clear out the existing credentials
$opts=$this->get_options();
$opts['tk_access_token']='';
unset($opts['tk_request_token']);
$opts['ownername']='';
// Set a flag so we know this authentication is in progress
$opts['auth_in_progress']=true;
$this->set_options($opts, true);
$this->set_instance_id($instance_id);
$this->bootstrap(false);
} catch (Exception $e) {
$this->log(sprintf(__("%s error: %s", 'updraftplus'), sprintf(__("%s authentication", 'updraftplus'), 'Dropbox'), $e->getMessage()), 'error');
}
}The do_authenticate_storage function above could be called from action_authenticate_storage function which will check the authentication is valid before proceeding to call the authentication method :
public function action_authenticate_storage() {
if (isset($_GET['updraftplus_'.$this->get_id().'auth']) && 'doit'==$_GET['updraftplus_'.$this->get_id().'auth'] && !empty($_GET['updraftplus_instance'])) {
$this->authenticate_storage((string) $_GET['updraftplus_instance']);
}
}Notice that the call to this->authenticate_storage function is supplied with raw value from $_GET['updraftplus_instance'] which will be directly echoed later without proper sanitization on the previous get_authentication_link function that we previously mentioned. The action_authenticate_storage function could be called from action_auth which handles various URL actions, as indicated from handle_url_actions function :
public function handle_url_actions() {
// First, basic security check: must be an admin page, with ability to manage options, with the right parameters
// Also, only on GET because WordPress on the options page repeats parameters sometimes when POST-ing via the _wp_referer field
if (isset($_SERVER['REQUEST_METHOD']) && ('GET'==$_SERVER['REQUEST_METHOD'] || 'POST'==$_SERVER['REQUEST_METHOD']) && isset($_GET['action'])) {
if (preg_match("/^updraftmethod-([a-z]+)-([a-z]+)$/", $_GET['action'], $matches) && file_exists(UPDRAFTPLUS_DIR.'/methods/'.$matches[1].'.php') && UpdraftPlus_Options::user_can_manage()) {
$_GET['page']='updraftplus';
$_REQUEST['page']='updraftplus';
$method=$matches[1];
$call_method="action_".$matches[2];
$storage_objects_and_ids=UpdraftPlus_Storage_Methods_Interface::get_storage_objects_and_ids(array($method));
$instance_id=isset($_GET['updraftplus_instance']) ? $_GET['updraftplus_instance'] : '';
if ("POST"==$_SERVER['REQUEST_METHOD'] && isset($_POST['state'])) {
$state=urldecode($_POST['state']);
} elseif (isset($_GET['state'])) {
$state=$_GET['state'];
}
// If we don't have an instance_id but the state is set then we are coming back to finish the auth and should extract the instance_id from the state
if (''==$instance_id && isset($state) && false !==strpos($state, ':')) {
$parts=explode(':', $state);
$instance_id=$parts[1];
}
if (isset($storage_objects_and_ids[$method]['instance_settings'][$instance_id])) {
$opts=$storage_objects_and_ids[$method]['instance_settings'][$instance_id];
$backup_obj=$storage_objects_and_ids[$method]['object'];
$backup_obj->set_options($opts, false, $instance_id);
} else {
updraft_try_include_file('methods/'.$method.'.php', 'include_once');
$call_class="UpdraftPlus_BackupModule_".$method;
$backup_obj=new $call_class;
}
$this->register_wp_http_option_hooks();
try {
if (method_exists($backup_obj, $call_method)) {
call_user_func(array($backup_obj, $call_method));
}
---------------------------------------------------------------------------------------The handle_url_actions will be set as a function handler to init hook and will call the corresponding backup method based on our supplied GET parameter.
The only missing part is where the plugin call the get_authentication_link function. Turns out the function could be called from get_method_auth_link which will setup the storage object and get the authentication link ready to be output with the notice :
public function get_method_auth_link($method) {
$storage_objects_and_ids=UpdraftPlus_Storage_Methods_Interface::get_storage_objects_and_ids(array($method));
$object=$storage_objects_and_ids[$method]['object'];
foreach ($this->auth_instance_ids[$method] as $instance_id) {
$object->set_instance_id($instance_id);
$this->show_admin_warning(''.__('UpdraftPlus notice:', 'updraftplus').' '.$object->get_authentication_link(false, false), 'updated updraft_authenticate_'.$method);
}
}The get_method_auth_link function will be called from show_admin_warning_dropbox which will act as function handler of all_admin_notices hook that will prints generic admin screen notices. This hook is guaranteed to display on all admin pages area no matter what, including multisite network admin pages.
Note that this vulnerability could be triggered on a default installation or configuration of UpdraftPlus plugin but required the WordPress site to choose Dropbox as remote storage option. Please also note that the CSRF could only be triggered from administrator role account by default and only need one visit of the crafted WordPress site URL to trigger the Site Wide XSS.
The patch in UpdraftPlus
The first issue is CSRF which due to lack of nonce validation, applying nonce check using wp_verify_nonce should fix the issues. The patch can be found below :
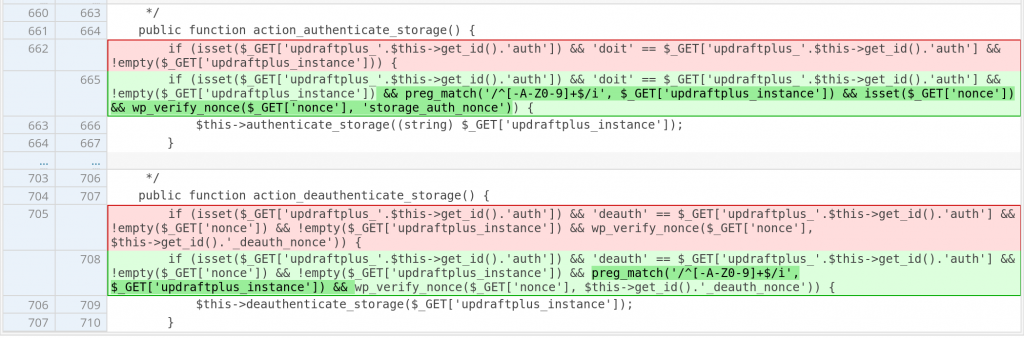
Notice that above patch also restrict the $_GET['updraftplus_instance'] parameter to a safe whitelist. The whitelisted character check also implemented on the build_authentication_link function. The patch can be found below :
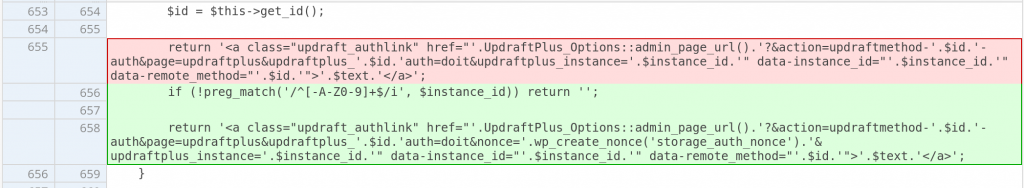
Conclusion
Always secure an action with permission and nonce validation if the action contain sensitive process or information. We could validate the permission using the current_user_can function and validate the nonce with the wp_verify_nonce function.
Also keep in mind to sanitize every value that being outputted to the front-end. We could utilize esc_html or esc_attr function, depending on the need. Another approach for sanitization could also applying a whitelisted HTML safe character.
Disclosure
12 May, 2023 – We found the vulnerability and reached out to the plugin vendor.
16 May, 2023 – UpdraftPlus plugin version 1.23.4 was published to patch the reported issues.
18 May, 2023 – Added the vulnerabilities to the Patchstack vulnerability database.
19 May, 2023 – Published the article.
Since we’ve detected that third-parties have had access to the vulnerability information via monitoring the changelog and have made the issue public, we’ve decided to disclose the vulnerability early.
Help us make the Internet a safer place
Making the WordPress ecosystem more secure is a team effort, and we believe that plugin developers and security researchers should work together.
- If you’re a plugin developer, join our mVDP program that makes it easier to report, manage and address vulnerabilities in your software.
- If you’re a security researcher, join Patchstack Alliance to report vulnerabilities & earn rewards.
Source: patchstack.com



