We’ve just released a new type of Patchstack reports – a downloadable website security report that makes it easy to get a periodic overview of a website’s security status. The new ‘Developer report‘ is available to Patchstack Developer and Business plan customers.
A simplified version of the report – the Snapshot report – is also available to Community plan users.
We’re also working on a ‘Client report’ (release date TBD) for our Business plan users, which will be focused on communicating completed maintenance work to their clients.
But we’re getting ahead of ourselves – for now, let’s take a look at what the ‘Developer reports’ look like!
How to access the Patchstack reports
You can find all reports under the ‘Reports’ tab in the sidebar when logged into the Patchstack App.
In order to generate a ‘Developer Reports’, simply choose the site you want to report on, pick a time frame and hit generate – a PDF of the report will be sent to your email!
What’s included in the Developer reports?
The main point of this report is to give you an overview of any outstanding security issues that may be affecting your site, along with a list of recommended actions to address those issues. These reports can be generated periodically and will also include an overview of suspicious activity in a given time frame.
The Developer report includes four important sections:
Suggested actions
This is a bird’s eye view of the most important issues on the site along with recommended actions to address those issues:
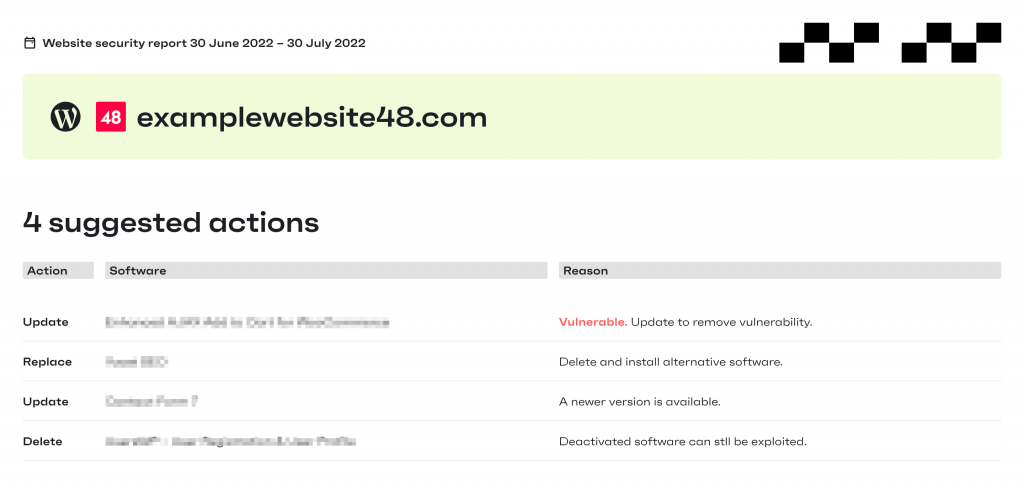 An example of suggested actions in the developer report
An example of suggested actions in the developer report
Security vulnerabilities
This is a list of all the website components that are vulnerable, along with information about the severity of those vulnerabilities and whether they are being actively exploited in the wild.
You can also see information about when the vulnerabilities were discovered, and which of them are mitigated by Patchstack:
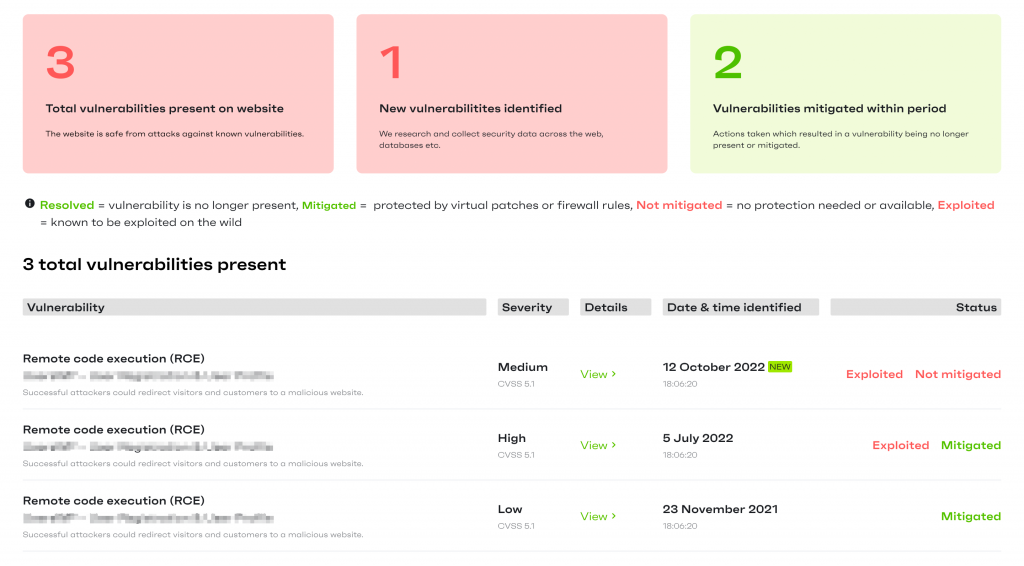
You may see some are not being mitigated, but usually, this means it’s a low-level bug that is very unlikely to be exploited under real-life circumstances, and no dedicated virtual patch exists for it.
Software overview
This section gives you a full list of all components installed on the website, along with their status – whether they are up-to-date, if they are activated on the site, etc.
Critically this section also tells you whether a plugin is likely to be abandoned – abandoned plugins are a serious security risk as they may contain bugs with no developer to address them. In fact, we found that last year 26% of new critical vulnerabilities never received a fix.
Firewall activity & blocked threats
Finally, you can also see how many threats were blocked in a given time period by virtual patches, generic firewall rules as well as custom ones.
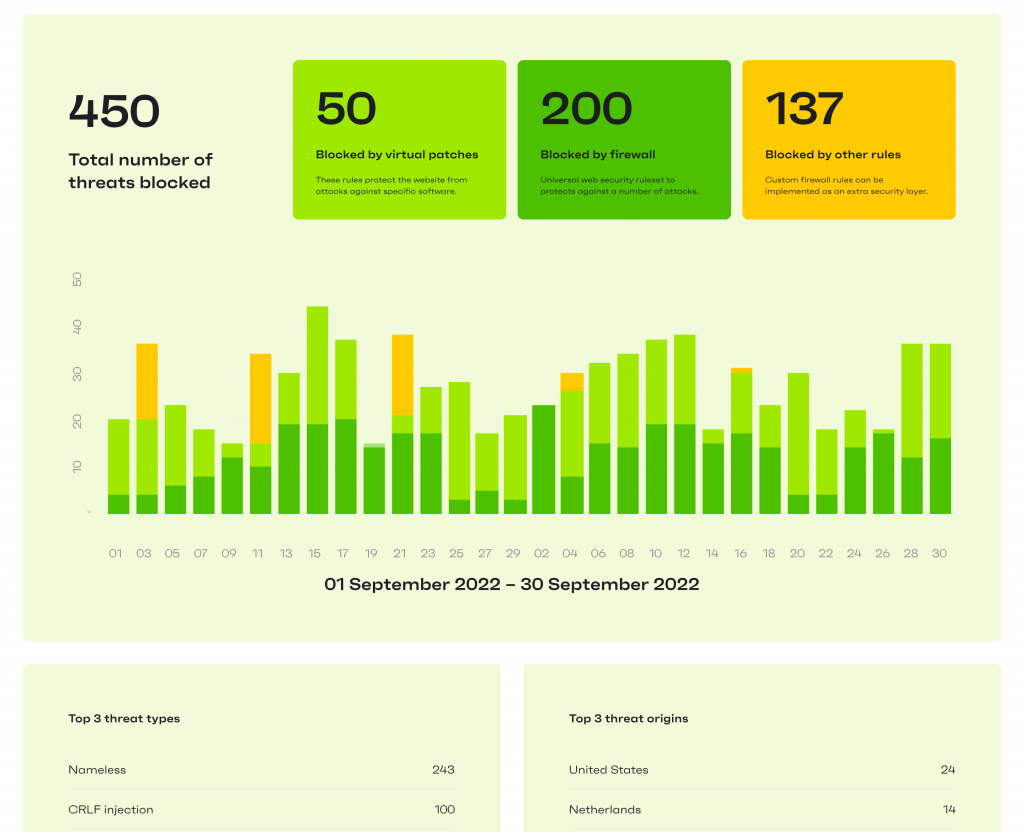
You can also see the most popular threats blocked, and also which countries most of these originated from.
Stay one step ahead of hackers
Patchstack helps website developers protect their websites against WordPress core, plugin, and theme vulnerabilities. We also offer general protection and hardening features to protect you from the most common attacks and help you manage the security and updates for all your sites from one convenient dashboard.
All of this – and the report above – is included in the Patchstack Developer plan. See pricing for more details!
You can view a preview of the full ‘Developer report’ here.
Source: patchstack.com



