For popular messengers such as Telegram, Signal and WhatsApp, there are quite a few alternative clients (not to be confused with clients as in (human) customers; whoever opted this confusing language needs a good talking to) out there. Such modified apps — known as mods — often provide users with features and capabilities that aren’t available in the official clients.
While WhatsApp disapproves of mods — periodically banning them from official app stores, not only has Telegram never waged war on alternative clients, it actively encourages their creation, so Telegram mods are popping up like mushrooms. But are they safe?
Alas, several recent studies show that messenger mods should be handled with great caution. Although most users still blindly trust any app that’s been verified and published on Google Play, we’ve repeatedly highlighted the dangers: when downloading an app on Google Play, you could also pick up a Trojan (that one had more than a 100 million downloads!), a backdoor, a malicious subscriber, and/or loads of other muck.
This just in: infected Telegram in Chinese and Uyghur on Google Play
We’ll start with a recent story. Our experts discovered several infected apps on Google Play under the guise of Uyghur, Simplified Chinese and Traditional Chinese versions of Telegram. The app descriptions are written in the respective languages and contain images very similar to those on the official Telegram page on Google Play.
To persuade users to download these mods instead of the official app, the developer claims that they work faster than other clients thanks to a distributed network of data centers around the world.
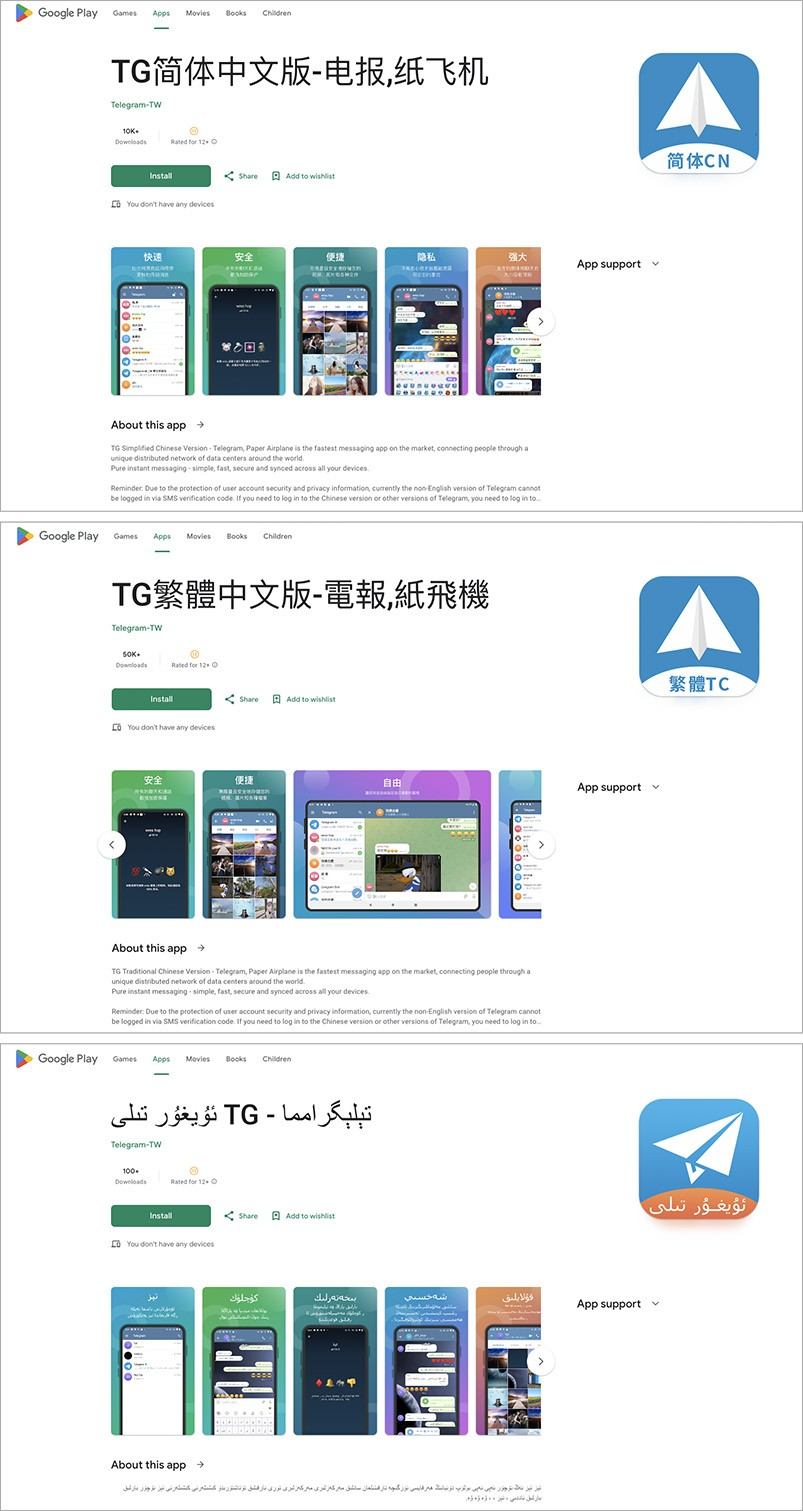
Simplified Chinese, Traditional Chinese, and Uyghur versions of Telegram on Google Play with spyware inside
At first glance, these apps appear to be full-fledged Telegram clones with a localized interface. Everything looks and works almost the same as the real thing.
We took a peep inside the code and found the apps to be little more than slightly modified versions of the official one. That said, there is a small difference that escaped the attention of the Google Play moderators: the infected versions house an additional module. It constantly monitors what’s happening in the messenger and sends masses of data to the spyware creators’ command-and-control server: all contacts, sent and received messages with attached files, names of chats/channels, name and phone number of the account owner — basically the user’s entire correspondence. Even if a user changes their name or phone number, this information also gets sent to the attackers.
Previously: spyware versions of Telegram and Signal on Google Play
Interestingly, a short while ago researchers at ESET found another spyware version of Telegram — FlyGram. True, this one didn’t even try to pretend to be official. Instead, it positioned itself as an alternative Telegram client (that is, just a mod), and had found its way not only onto Google Play, but into the Samsung Galaxy Store as well.
What’s even more curious is that its creators didn’t limit themselves to imitating just Telegram. They also published an infected version of Signal in these same stores, calling it Signal Plus Messenger. And for added credibility, they even went so far as to create the websites flygram[.]org and signalplus[.]org for their fake apps.
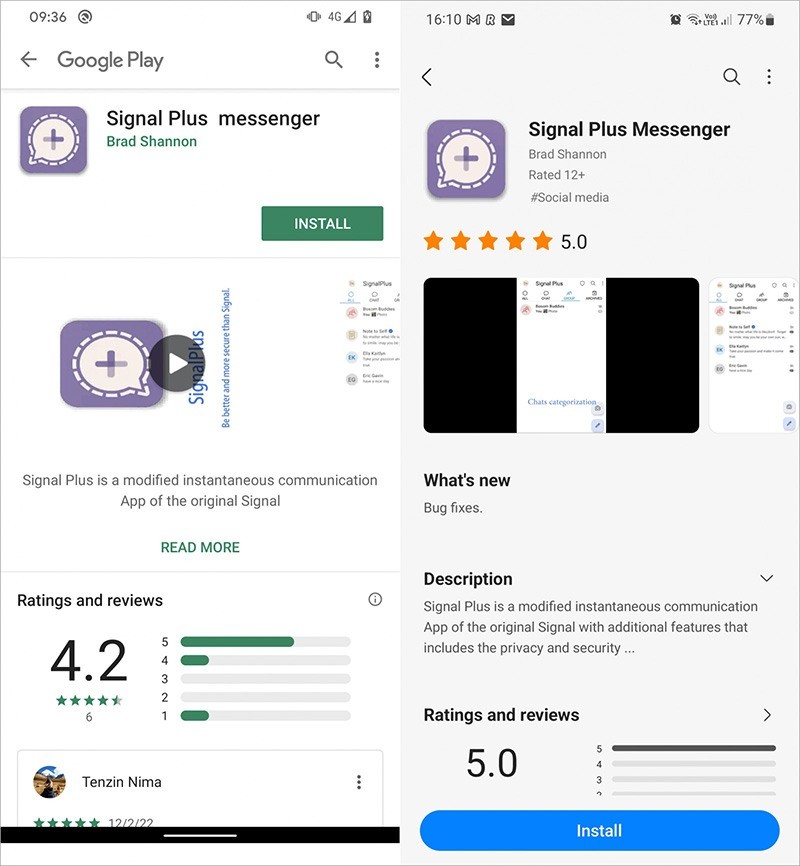
There’s a spyware client on Google Play for Signal too, called Signal Plus Messenger. (Source)
Inside, these apps amounted to full-fledged Telegram/Signal messengers, whose open-source code was flavored with malicious additives.
Thus FlyGram learned to steal contacts, call history, a list of Google accounts and other information from the victim’s smartphone, as well as make “backup copies” of correspondence to be stored… where else but on the attackers’ server (although this “option” had to be activated in the modified messenger independently by the user).
In the case of Signal Plus, the approach was somewhat different. The malware scraped a certain amount of information from the victim’s smartphone directly, and allowed the attackers to log in to the victim’s Signal account from their own devices without being noticed, after which they could read all correspondence almost in real time.
FlyGram appeared on Google Play in July 2020 and stayed there until January 2021, while Signal Plus was published in app stores in July 2022 and removed from Google Play only in May 2023. In the Samsung Galaxy Store, according to BleepingComputer, both apps were still available at the end of August 2023. Even if they are now completely gone from these stores, how many unsuspecting users continue to use these “quick and easy” messenger mods that expose all their messages to prying eyes?
Infected WhatsApp and Telegram spoof cryptowallet addresses
And just a few months back, the same security researchers uncovered a slew of trojanized versions of WhatsApp and Telegram aimed primarily at cryptocurrency theft. They work by spoofing the cryptowallet addresses in the messages so as to intercept incoming transfers.
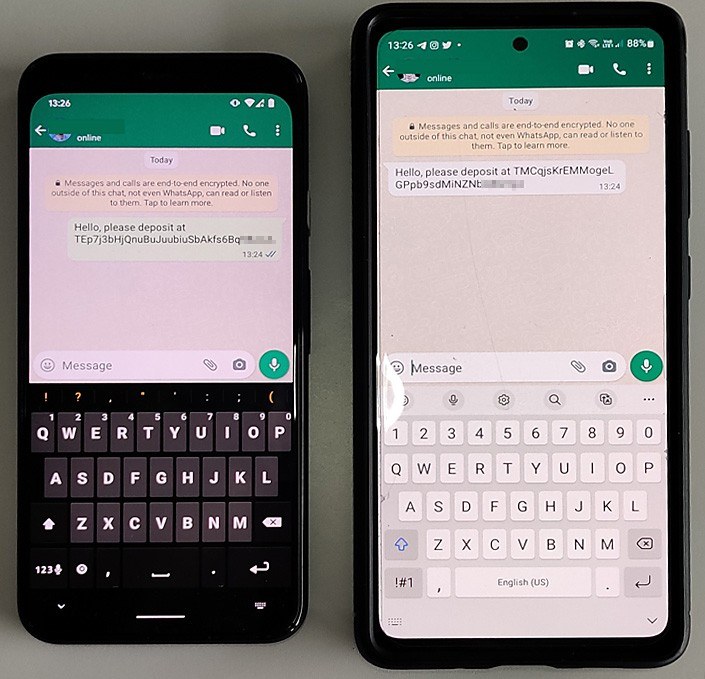
An infected version of WhatsApp (left) spoofs the cryptowallet address in a message to the recipient, who has the official, uninfected version of WhatsApp (right). (Source)
In addition, some of the versions found use image recognition to search screenshots stored in the smartphone’s memory for seed phrases — a series of code words that can be used to gain full control over a cryptowallet and then empty it.
And some of the fake Telegram apps stole user profile information stored in the Telegram cloud: configuration files, phone numbers, contacts, messages, sent/received files, and so on. Basically, they pilfered all user data except for secret chats created on other devices. All these apps were distributed not on Google Play, but through a variety of fake sites and YouTube channels.
How to stay safe
Lastly, a few tips on how to protect yourself from infected versions of popular messengers, as well as other threats targeting Android users:
- As we’ve seen, even Google Play isn’t immune to malware. That said, official stores are still far safer than other sources. So, always use them to download and install apps.
- As this post has made clear, alternative clients for popular messengers should be treated with extreme caution. Open source lets anyone create mods — and fill them with all sorts of nasty surprises.
- Before installing even the most official app from the most official store, look closely at its page and make sure that it’s real — pay attention not only to the name, but also the developer. Cybercriminals often try to fool users by making clones of apps with descriptions similar to the original.
- It’s a good idea to read negative user reviews — if there’s a problem with an app, most likely someone will have already spotted and written about it.
- And be sure to install reliable protection on all your Android devices, which will warn you if malware tries to sneak in.
- If you use the free version of Kaspersky: Antivirus & VPN, remember to manually scan your device after installation and before running any app for the first time.
- Threat scanning is done automatically in the full version of our security solution for Android, which is included into the Kaspersky Standard, Kaspersky Plus, and Kaspersky Premium subscription plans.
Source: kaspersky.com



