[Updated on June 28, 2017]
It looks like 2016 should be declared a year of ransomware, as new families and new versions are popping up every now and then like mushrooms after the rain.
Ransomware is evolving — fast. The new versions of ransomware use strong asymmetrical encryption with long keys so that files cannot be decrypted without the key. The bad guys have started using TOR and payments in bitcoins for the sake of staying totally anonymous. And now there is Petya ransomware which in a certain sense encrypts the whole hard drive all at once instead of encrypting files one by one.
How Petya gets his hands on your PC
Petya is a piece of ransomware that targets mostly business users, as it is distributed in spam emails that pretend to contain job applications. The standard infection scenario looks like this:
An HR employee receives an email from some person seeking a position in the company. The email contains a Dropbox link to a file which pretends to be their curriculum vitae but in reality it’s an EXE file.
Petya #ransomware encrypts master file table via @threatpost https://t.co/kCpbUcT1kV pic.twitter.com/9e6YjTkEVV
— Kaspersky Lab (@kaspersky) March 28, 2016
They click on the file, but never get a CV that they are supposed to find there. Instead they get a Blue Screen of Death. That means Petya has made its way into the user’s PC and started its dirty work.
Your hard drive belongs to us
Common ransomware usually encrypts files of certain types — pictures, Office documents and so on — and leaves the operating system unharmed so that the victim could use the PC to pay the ransom. But Petya is much more brutal as it aims to block access to the whole hard drive.
In a nutshell, no matter how your hard drive is organized, whether there is only one partition or more, there’s always some disk space invisible for you called Master Boot Record (MBR). It contains all the data on the number and organization of partitions, and it also contains a special code used to start booting the OS — it’s called boot loader.
This boot loader always runs BEFORE the operating system. And this is exactly what Petya infects: it modifies boot loader so that it loads Petya’s malicious code instead of any operating system installed on the PC.
Researchers Learning More About #Petya Ransomware: https://t.co/WwOQ1mEsRb pic.twitter.com/O4TaS593ta
— Kaspersky Lab (@kaspersky) March 29, 2016
For the user it looks like Check Disk is running, which is pretty much OK after an operating system crash. But what Petya actually does at this moment is it encrypts Master File Table. That is yet another hidden part of your hard drive’s personal life. This table contains all the information about how files and folders are allocated.
Think of your hard drive as a vast library which contains millions or even billions of items. And the Master File Table is a library index. Well, that explanation is greatly simplified, let’s make it more realistic: on your hard drive ‘books’ are rarely stored as detached items, but rather as single pages or even scraps of paper. In heaps. No, not in any particular order, it’s pretty much random.
Perhaps now you have a general idea how uneasy it would be to find a single ‘book’ if someone had stolen this ‘library index – this is exactly what Petya ransomware does.
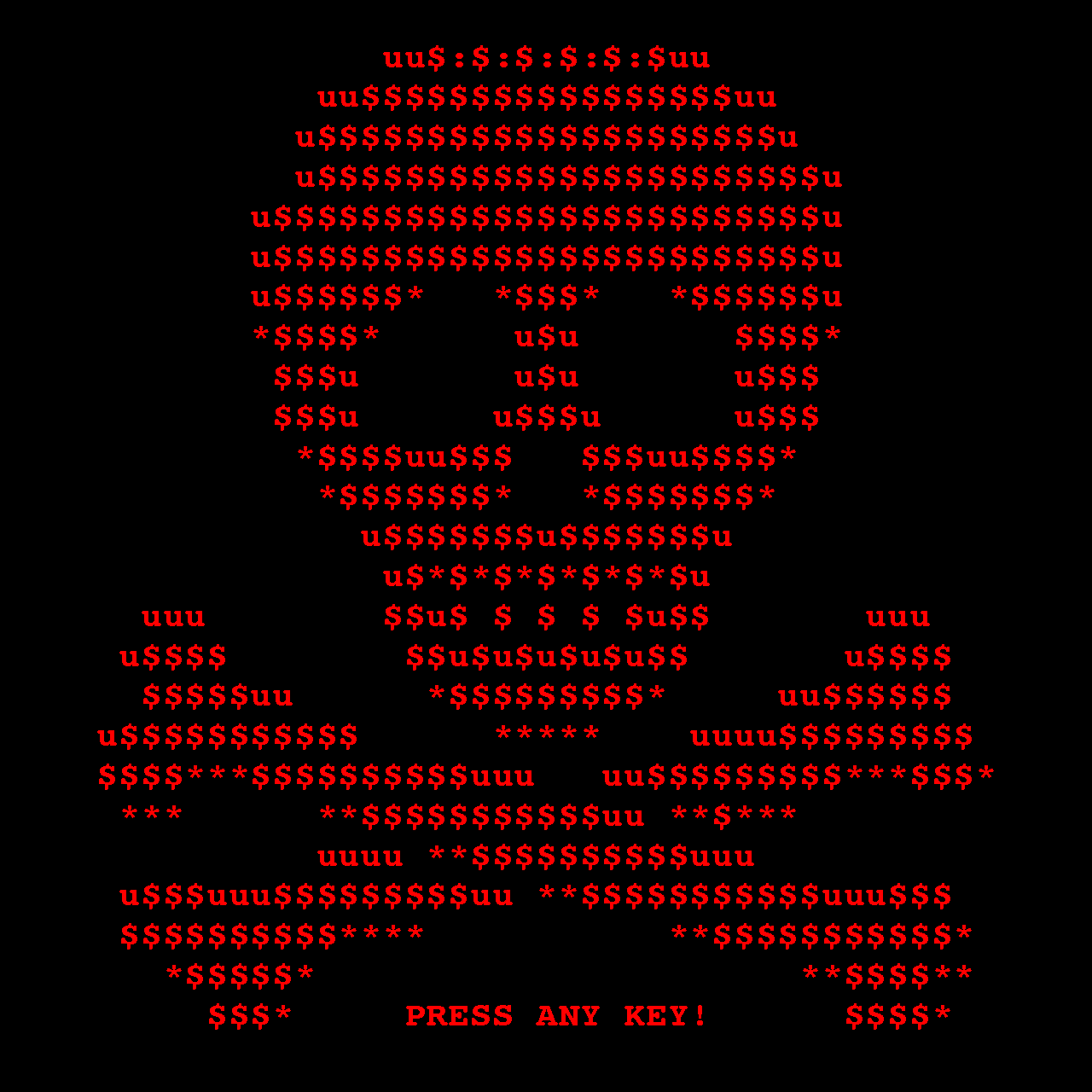
Once it’s done, Petya reveals its true face that looks like a skull built with ASCII symbols. Then the usual routine begins: the malware requires that the user has to pay a ransom (0.9 bitcoins which is about $380) if you want to decrypt the hard drive and get your files back.
The only difference from other ransomware is that Petya is completely offline, which is no surprise since it had ‘eaten’ the operating system. So the user has to find another computer in order to pay the ransom and get their data back.
Let's talk #Ransomware. Would you pay the #hackers ransom?
— Kaspersky Lab (@kaspersky) March 29, 2016
Fighting Petya
Unfortunately, as with other recent types of ransomware, researchers still haven’t found a way to decrypt information encrypted by Petya. However, there are still a few thing you can do to protect yourself and your data and some good news regarding Petya’s distribution.
The good news is that Dropbox has removed the malicious archives with Petya from its cloud storage. So now the bad guys have to find some other way of distribution. The bad news is that it probably won’t take them long to do that.
10 tips to protect your files from ransomware https://t.co/o0IpUU9CHb #iteducation pic.twitter.com/I47sPIiWFF
— Kaspersky Lab (@kaspersky) November 30, 2015
So, let’s get back to protection. What can you do?
1. When the user sees the Blue Screen of Death, all their data is still not corrupted, since Petya hasn’t started to encrypt the Master File Table. So if you see that your computer shows you a BSOD, reboots and starts the Check Disk — immediately shut it down. At this point you still can remove your hard drive, connect it to another computer (but don’t use it as a boot device!) and recover your files.
2. Petya encrypts only the MFT leaving the files themselves untouched. Files still can be recovered by specialists in hard drives recovery. This procedure would be intricate and time-consuming and it will cost you a pretty penny, but basically it is doable. However don’t try to do it at home — a mistake can make your files gone forever.
3. The best way is to protect yourself proactively using a good security solution. Kaspersky Internet Security won’t get the spam emails through, so you probably won’t even see the email containing the link to Petya. Even if Petya somehow sneaks in, it would be detected as Trojan-Ransom.Win32.Petr and Kaspersky Internet Security would block all its activities. And so would all the other our anti-virus solutions.
Update from June 28, 2017
If you’re looking for information regarding the new Petya / NotPetya / ExPetr ransomware outbreak, we have a dedicated post with advice on how to protect your files.
Source: kaspersky.com



