This year, news of ransomware attacks have been coming in like dispatches from a battlefield — nonstop. Every day, researchers find new strains of ransomware and discover new and unconventional ways criminals use it to steal money directly from consumers and businesses. And as soon as security experts make some progress, the crooks come up with new ransomware approaches and techniques.
Recently, another sophisticated sample of a ransomware was discovered. The malware is dubbed Satana (“Satan”), which might imply Russian-speaking origins. The Trojan does two things: It encrypts files and corrupts Windows’ Master Boot Record (MBR), thus blocking the Windows boot process.
We have already discussed Trojans that mess with the MBR — the notorious Petya ransomware is one such malware. In some ways, Satana behaves similarly, for example injecting its own code into the MBR. However, whereas Petya encrypts the Master File Table (MFT), Satana encrypts the MBR. To encrypt PC files, Petya relied on the help of a tagalong Trojan called Mischa; Satana manages both tasks on its own.
#Petya #ransomware eats your hard drives – https://t.co/BSqbmRBmGf pic.twitter.com/WpvijrPlSP
— Kaspersky (@kaspersky) March 30, 2016
For those who aren’t familiar with the inner workings of computers, we’ll try to shed some more light. The MBR is a part of the hard drive. It contains information on the file system used by different disk partitions, as well as which partition the operating system is stored on.
If the MBR becomes corrupted — or gets encrypted — the computer loses access to a critical piece of information: which partition contains the operating system. If the computer can’t find the operating system, it can’t boot. The malefactors behind ransomware like Satana took advantage of this arrangement and enhanced their cryptolocker with bootlocker capabilities. The hackers swap out the MBR, replacing it with the code of the ransom note, and encrypt and move the MBR somewhere else.
The ransomware demands about 0.5 bitcoins (approximately $340) to decrypt the MBR and provide the key to decrypt the affected files. Once the ransom is paid, Satana’s creators say, they will restore access to the operating system and make things look just as they did before. At least, that’s what they say.
Once it’s inside the system, Satana scans all drives and network instances, looking for .bak, .doc, .jpg, .jpe, .txt, .tex, .dbf, .db, .xls, .cry, .xml, .vsd, .pdf, .csv, .bmp, .tif, .1cd, .tax, .gif, .gbr, .png, .mdb, .mdf, .sdf, .dwg, .dxf, .dgn, .stl, .gho, .v2i, .3ds, .ma, .ppt, .acc, .vpd, .odt, .ods, .rar, .zip, .7z, .cpp, .pas, and .asm files, and starts encrypting them. It also adds an e-mail address and three underscore symbols to the beginning of the file name (for example, test.jpg would become [email protected]___test.jpg).
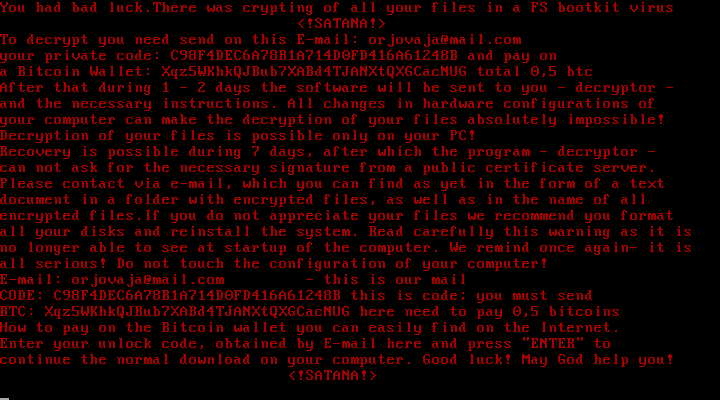
The e-mail addresses are meant to serve as contact information for the victims, who are supposed to write to the address to get payment instructions and then retrieve the decryption key. So far, researches have seen six e-mail addresses used in this campaign.
The good news is that it is possible to partially bypass the lock: With certain skills, the MBR can be fixed. Experts at The Windows Club blog produced detailed instructions on how to fix the MBR by using the OS restore feature in Windows. However, that feature is designed for experienced users who are comfortable working with the command prompt and the bootrec.exe utility; an ordinary user is not likely to nail this cumbersome method straight away and may not feel comfortable trying.
The bad news is that even with Windows successfully unlocked, the other half of the problem, encrypted files, remains. No cure is available for that part yet.
At this point, Satana seems to have just started its ransomware career: It’s not widespread, and researchers have spotted some flaws in its code. However, there is a good chance that it will improve over time and evolve into a very serious threat.
10 tips to protect your files from ransomware https://t.co/o0IpUU9CHb #iteducation pic.twitter.com/I47sPIiWFF
— Kaspersky (@kaspersky) November 30, 2015
Our primary advice to users for now is to practice constant vigilance. Our simple recommendations will help to lower your risk of infection and keep you away from trouble as much as possible:
1. Back up your data regularly
This is your insurance policy. In the case of a successful ransomware attack, you can just reinstall the operating system and retrieve files from the backup copies.
2. Don’t visit suspicious websites and don’t open suspicious e-mail attachments, even if you got the link or e-mail from a person you know. Be very cautious: Little is known about Satana’s propagation techniques.
3. Make sure to use a reliable antivirus solution. Kaspersky Internet Security detects Satana as Trojan-Ransom.Win32.Satan and prevents it from encrypting files or locking the system.
4. And, of course, follow our news!
We’ll always try to tell you about the newest threats as soon as possible, so malware doesn’t catch you unawares.
Source: kaspersky.com



